Preface
Windows server update services (WSUS) retrieves Windows and other Microsoft products (such as office application products) updates and store them internally as a distribution point. So, it is not hectic for bandwidth consumption as each Microsoft device does not have to contact Microsoft servers for the update. WSUS is also a valid source if we consider a security point of view as well. The WSUS is a distribution point for local Windows servers and workstations to get the security and other updates from Microsoft servers. The WSUS servers can act as replica servers where the replica copies of Microsoft updates fetch from a central WSUS server and distribute the updates for a subnet or site. WSUS services can be used for testing updates before it approved for a server or workstation.
In this article, I am going to demonstrate how to deploy Microsoft Windows Server Update Services from the Windows server role group and configure to synchronize patches from Microsoft update servers. We are also going to look at how to configure Group Policy Object to auto-update the approved windows patches from the WSUS server and schedule the restart after the update installation. We are going to configure client-side targeting to group the computers to a specific target name so that it will be easier for administrators to troubleshoot or update the systems.
The following points are discussed in this article while demonstrating the WSUS role installation. I would recommend going through this article step by step for the audience who are new to this concept called WSUS. But for experienced administrators, you can go to the configuration step where you are stuck at configuring. Let us begin the installation and when you are ready with the server installed Windows server 2019 and joined to the Active Directory domain.
- Add Windows Server Update Services role
- WSUS Configuration Wizard
- Launch Windows Server Update Services Console
- Configure the Group Policy object for WSUS Clients
- Testing WSUS Client
Add Windows Server Update Services role
The demonstration begins with installing the WSUS role from the Windows server 2019 role group from the server manager snap-in. Launch server manager and click on Add roles and features to start adding the server role.
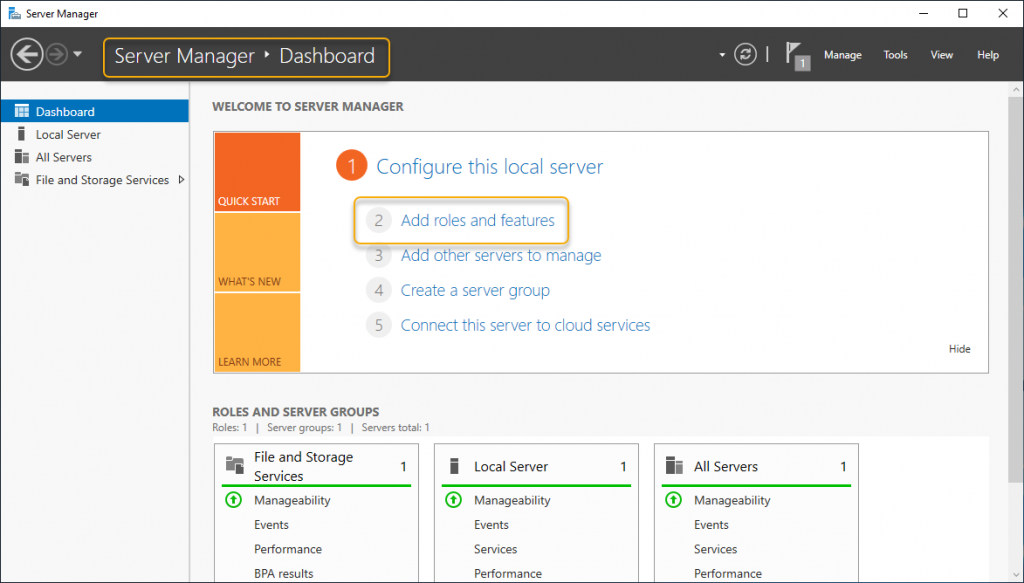
The wizard instructions give you a gist of how the Add roles and features wizard help you install the roles or features to your local or remote computer. You may go through the instruction if you are new to add roles and features of Windows Server. If you don’t want to see “before you begin page” anymore, click skip this page and click next to move on to the next page of the wizard.
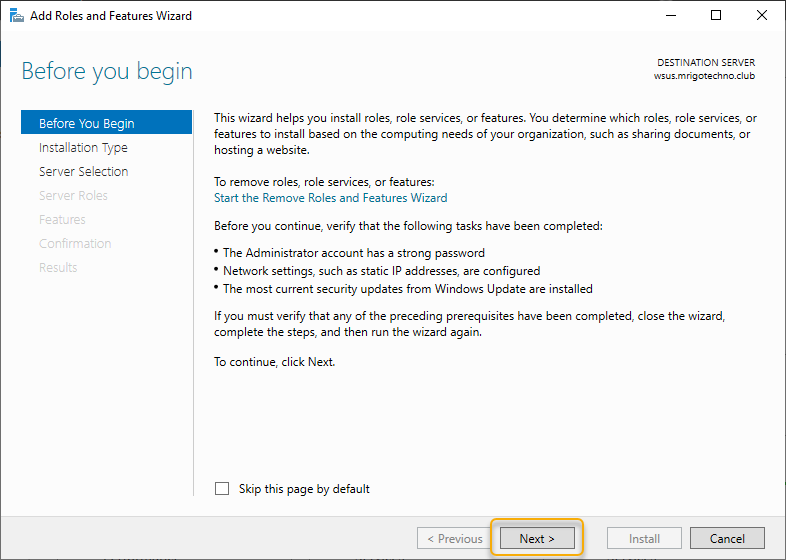
The WSUS role comes under role-based or feature-based installation. So, click Role-Based or Feature-Based installation and click Next.
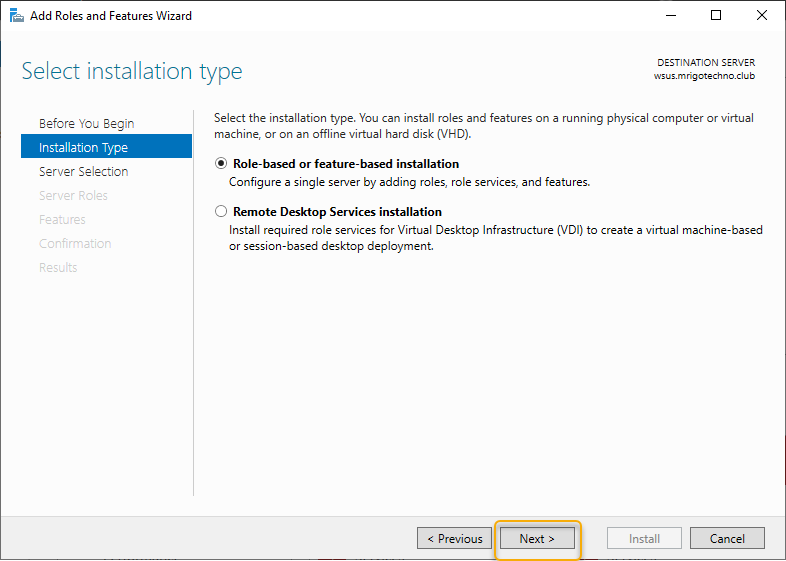
On the server selection, the local server listed, and our intention is also to install the WSUS role on the local server. Click Next to continue.
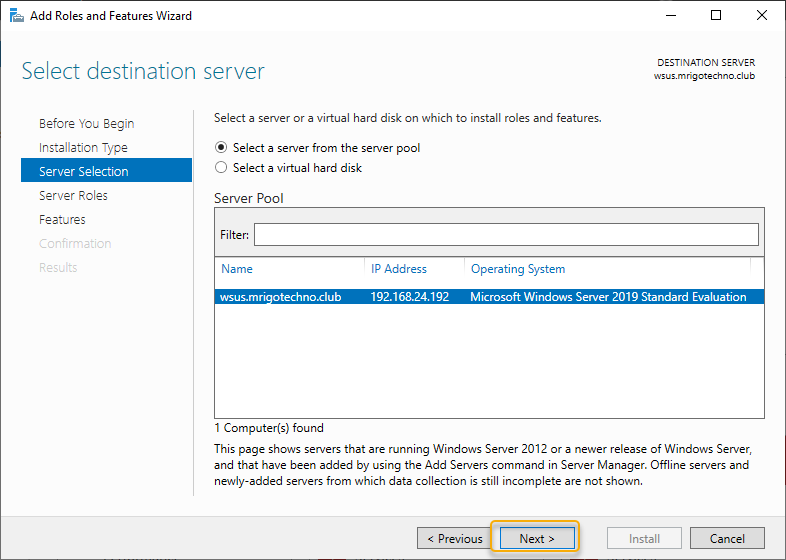
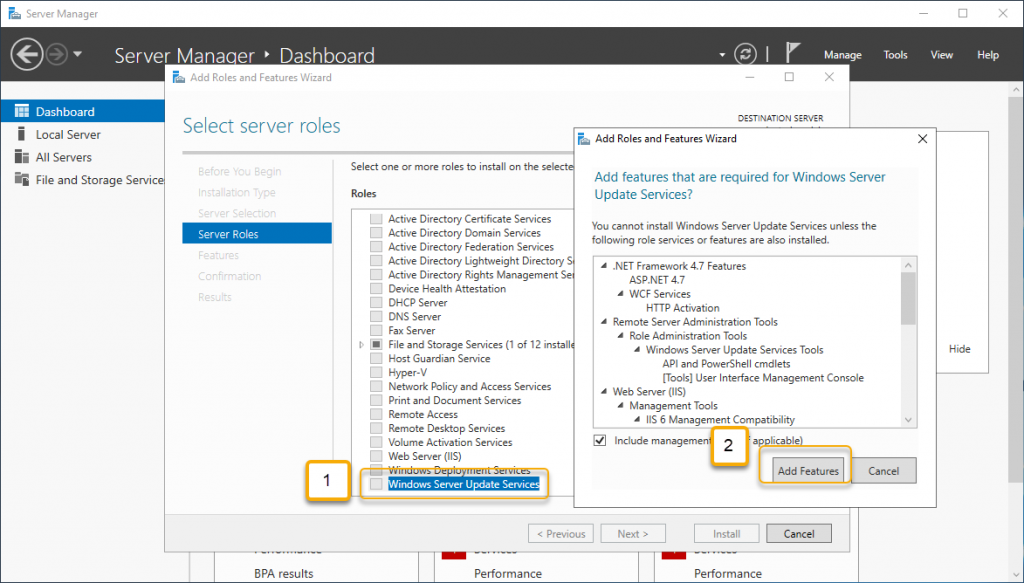
From the server roles list, select Windows Server Update Services, and when you click on the role, you will be prompted to choose the features to install, leave the default selection and click Add Features to return to the role selection window.
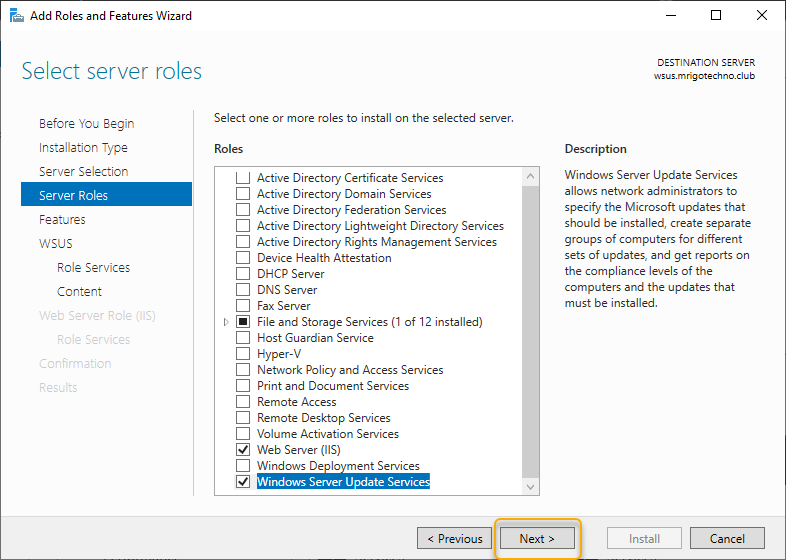
As the Windows Server Update Services role with checkbox selected, click Next to continue.
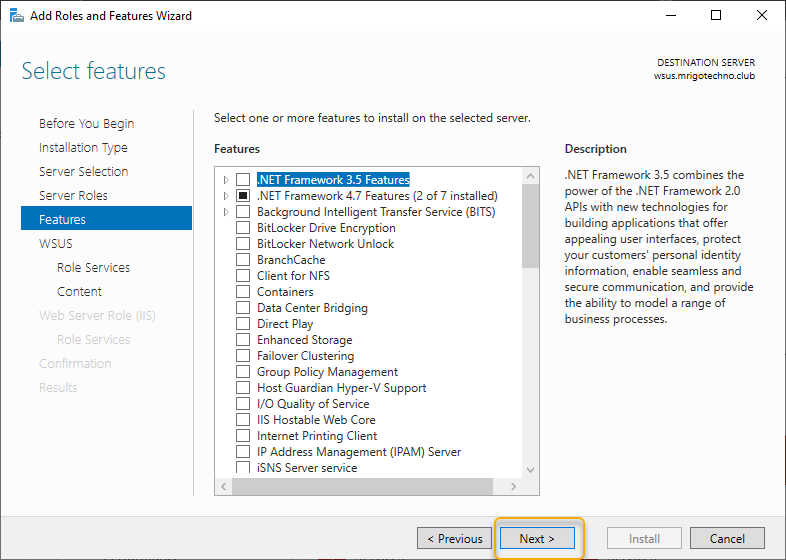
The next screen is to select features related to the role, leave the default selection, and click Next.
On the WSUS page, the instruction of WSUS would be given, go through the WSUS instruction, and click Next to continue.
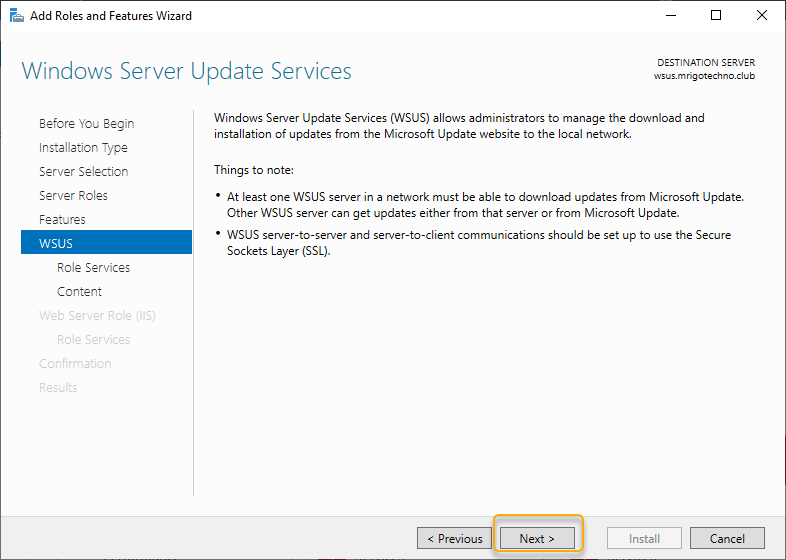
On the select role service page, leave the WID connectivity and WSUS roles selected, and move on to the next page by clicking Next.
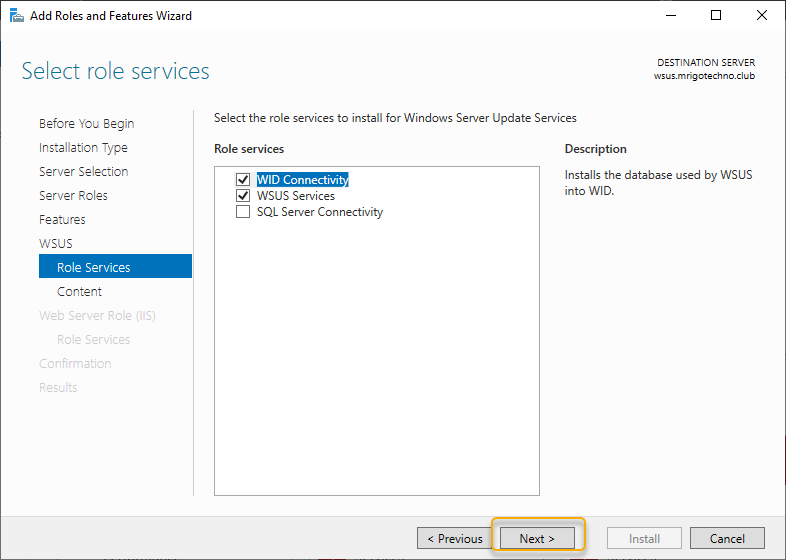
On the content location selection, give a path to a drive that has at least 50 GB disk space and enough space to grow as your update selection. It is also a good idea to select a keep the content away from the system drive. As this is a demonstration, I have pointed C:\WSUS as a content path. Type the folder path and click Next to continue.
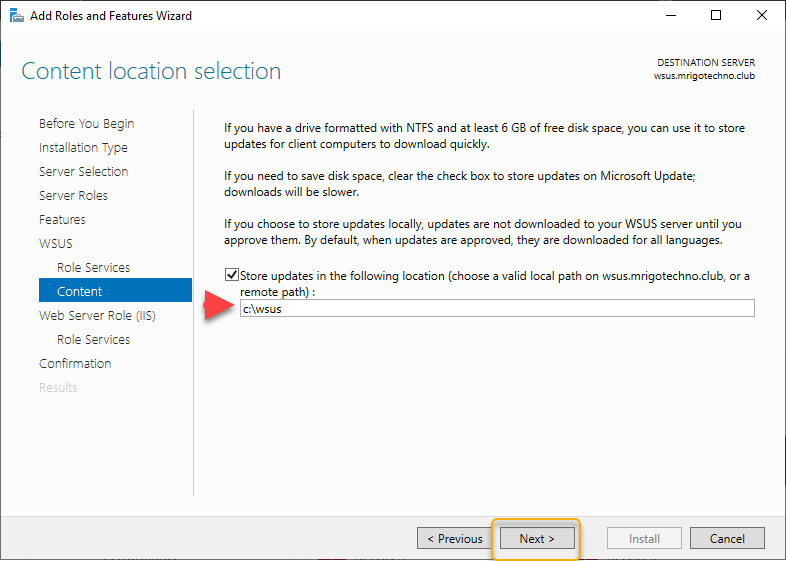
The WSUS clients such as Windows client workstations and Windows Servers mostly depend on Web services of WSUS for connectivity. For detailed information, you may go through the details on this page and click Next to continue.
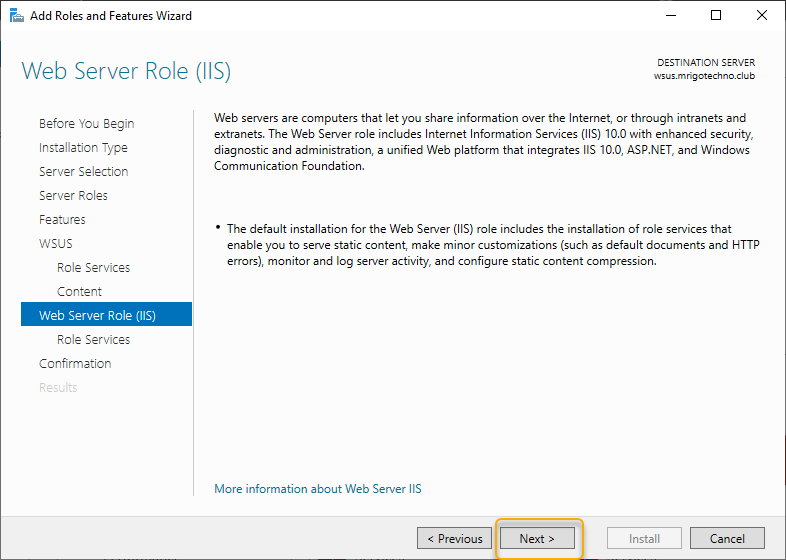
On the Role Services page, leave the default selection and click Next to continue.
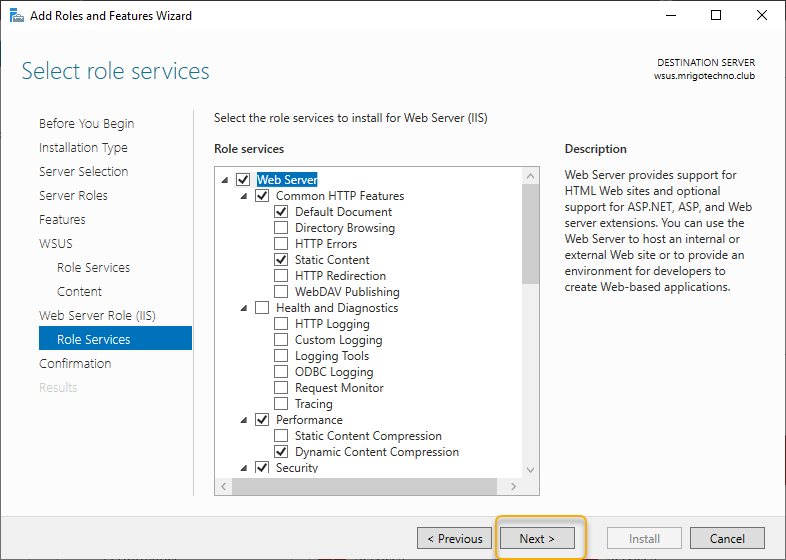
On the confirmation page, you would see all the roles and features selected so far to install the WSUS role, click install to start the installation.
The view installation progress, let you know the installation progress of the installation, leave the WSUS installation to complete.
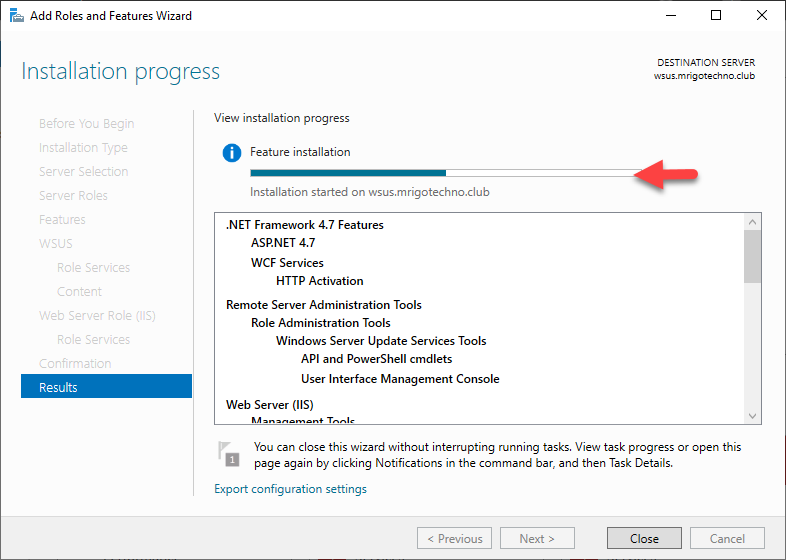
Once the installation completed, you would see launch post-installation, click post-installation to start.
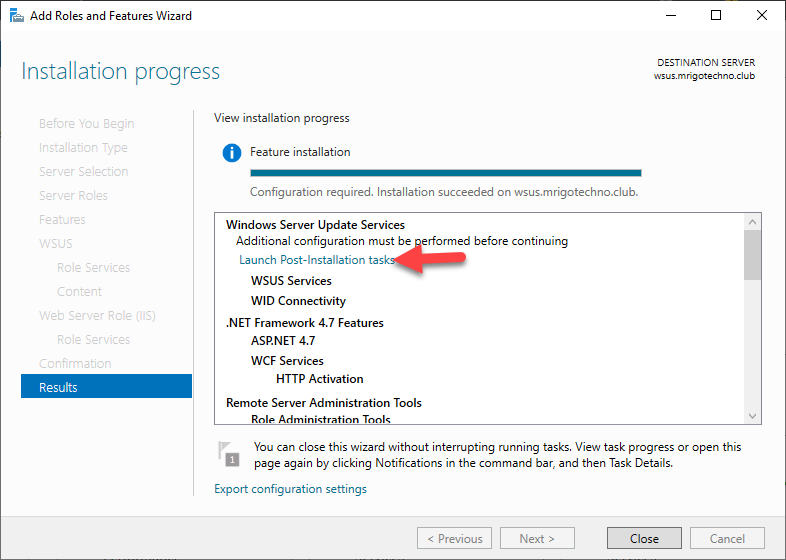
Click the notification flag to check the post-installation progress and status of it. After about two minutes, you would get the state as installation succeeded.
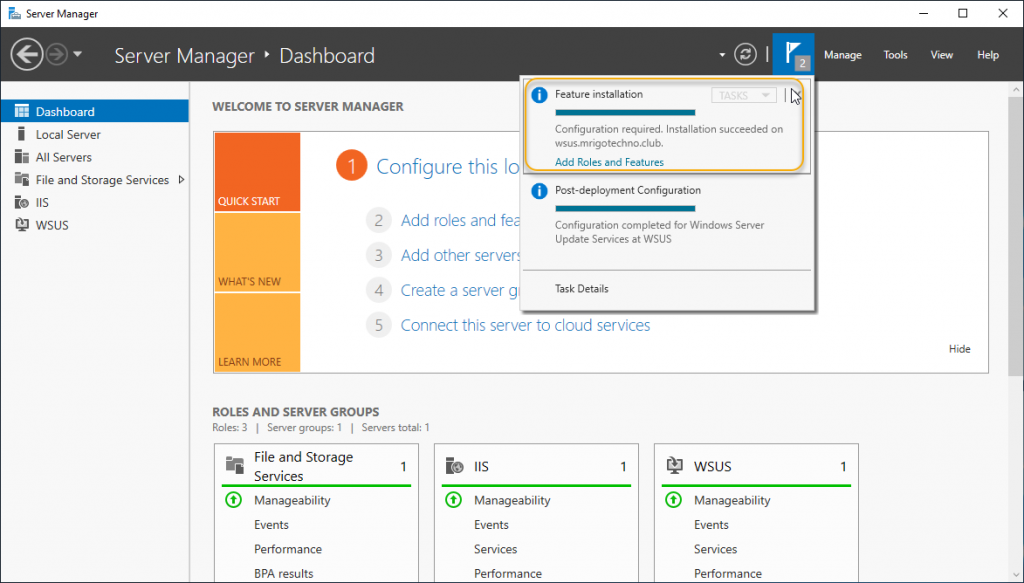
WSUS Configuration Wizard
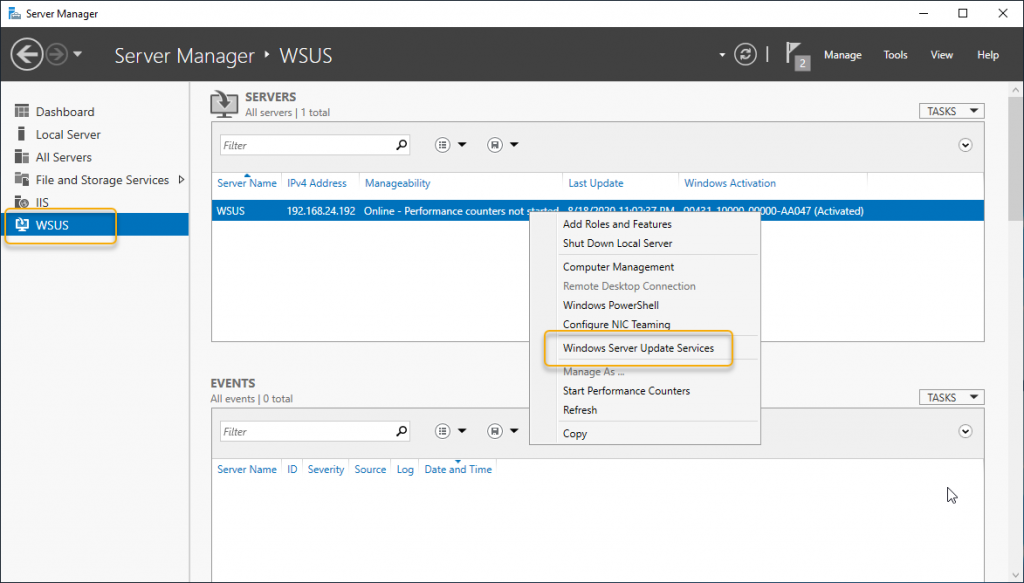
Select the WSUS role from the left side navigation and right-click the server and click Windows Server Update Services to start the WSUS configuration wizard.
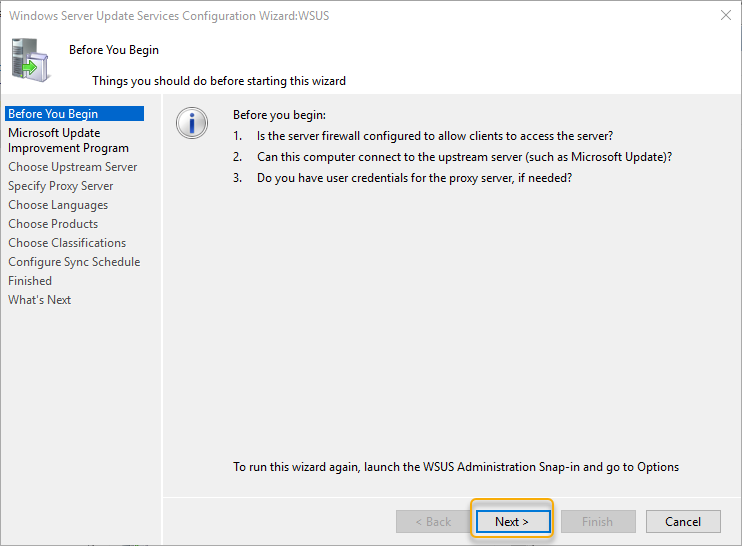
On the before you begin page, there are some questions prompted to check if the firewall allowed to access the clients, connectivity to the internet to access the Microsoft servers to download the updates, and in there is any proxy server credentials to access the Microsoft servers. Go through the questions and get on them if required and click Next to continue.
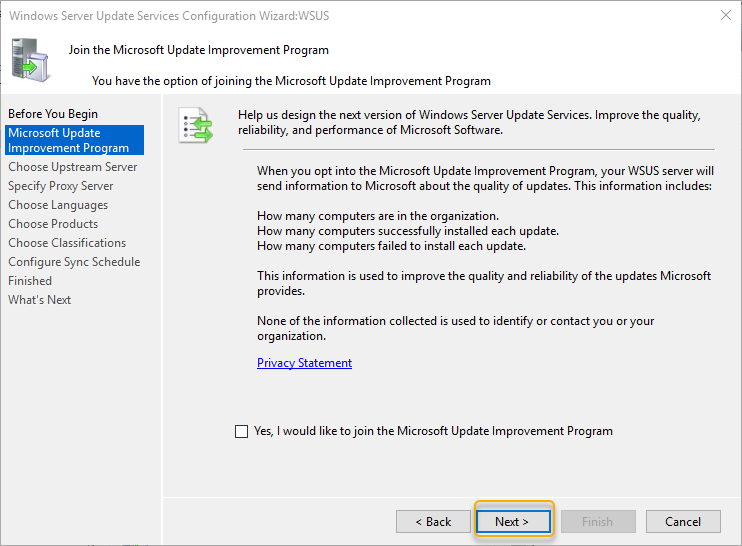
As this is a demonstration, I have unchecked the Microsoft update improvement program to participate. You can choose either to join or not, whatever you wish. Click next to continue.
This server is going to get the updates from the Microsoft Server, so select synchronize from Microsoft update and click next.
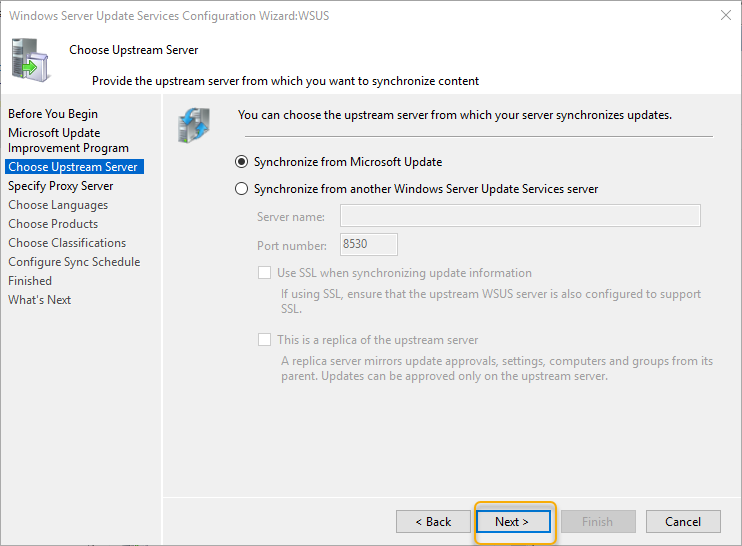
If you are using a proxy server to access the internet, type the proxy server details. Mostly the internet is connected directly, click Next to continue.
The next page is to connect the upstream server; this will take about ten minutes to complete the connection, wait for the server to connect to the upstream server.
The connection progress will give you the status of the connectivity, wait for the connection to happen to the upstream server.
Once the connectivity has completed connection to the upstream server, click Next to continue.
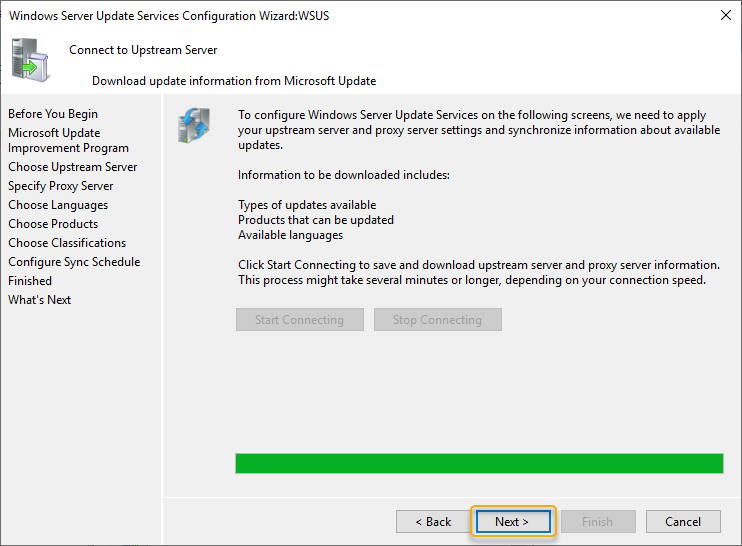
As all Microsoft systems installed with the English language in my lab network, I have selected English. In your installation, if multiple languages are needed or any specific language to choose, select the appropriate language, and click Next.
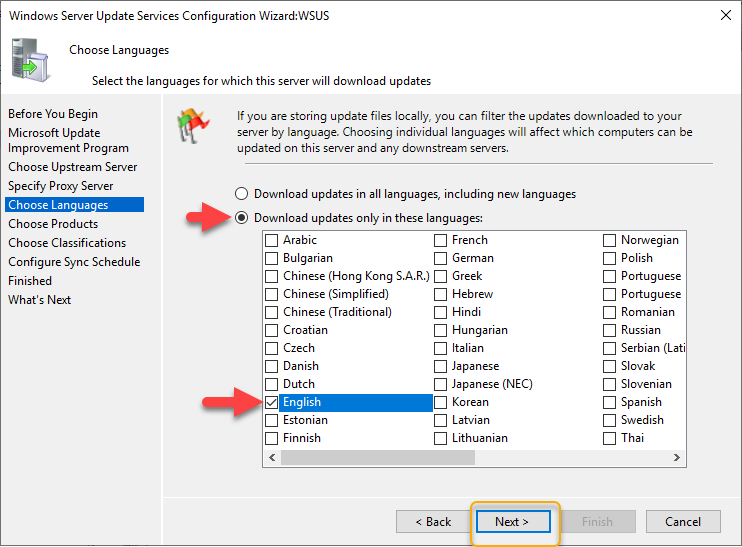
In this demonstration, I’m using a Windows 10 computer to test the Windows update settings, and you can go through the list and choose the appropriate selection for other windows to update such as Windows Server 2019, Office pro plus, and so on. Click Next to continue.
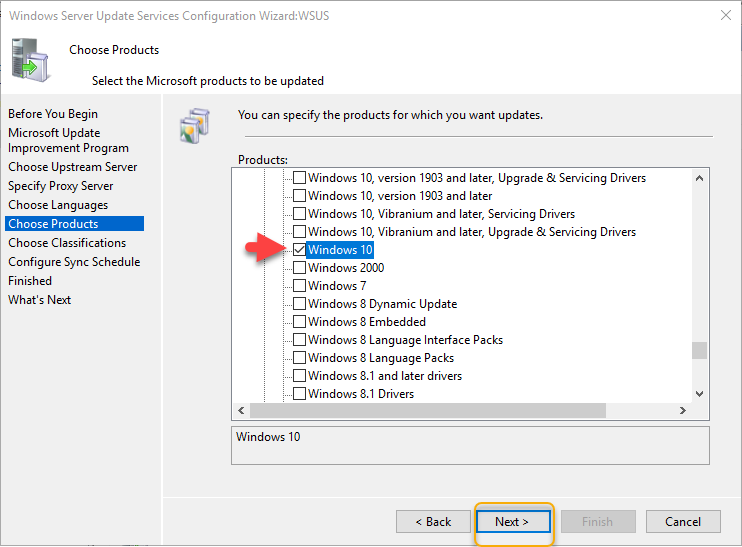
Select the updates as you need, I have selected Critical, definition, and security updates. You may also choose updates such as upgrades, drivers, and so on. Click Next to continue.
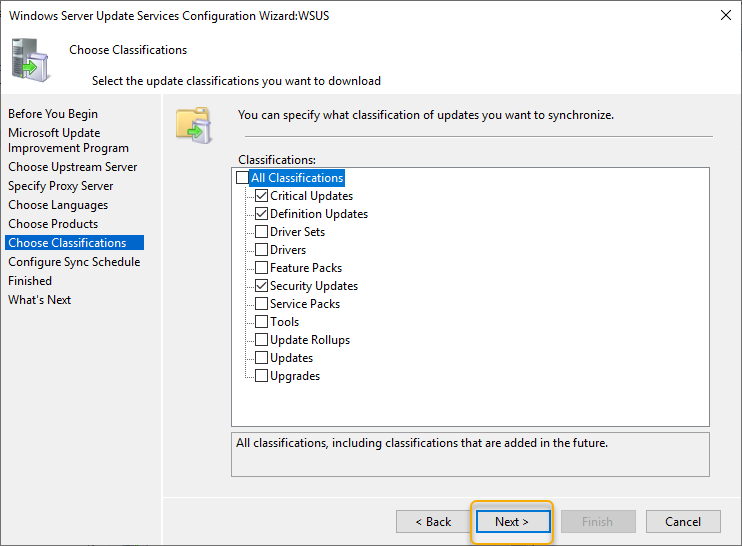
On the Synchronization schedule, select “synchrone automatically” and choose a time suitable for synchronization to happen, also windows update synchronization per day, default is 1. Select a time in the early morning window will be a good idea. Click Next to continue
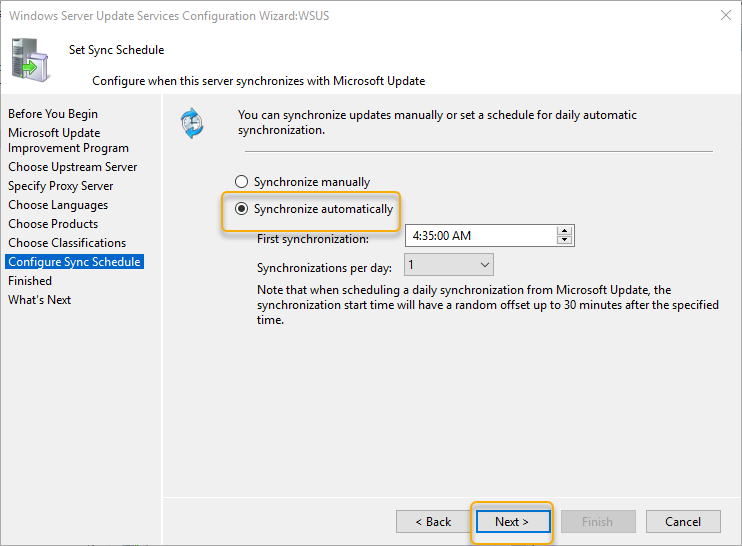
On the Finished page, Select Begin initial synchronization and click Next.
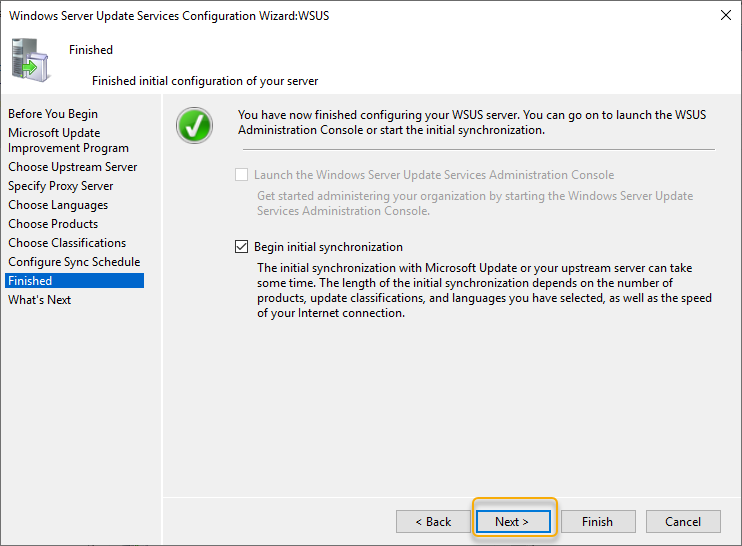
On the what’s next page, click finish to end the WSUS configuration wizard and launch WSUS.
Launch Windows Server Update Services Console
The next is to go to the server manager and select the WSUS role on the left side navigation and right-click the server from the middle pane and click Windows Server Update Services.
On the updates tab, expand it and select critical updates and change the status to any on the top filtering options and click refresh. You would see the critical updates available for installation.
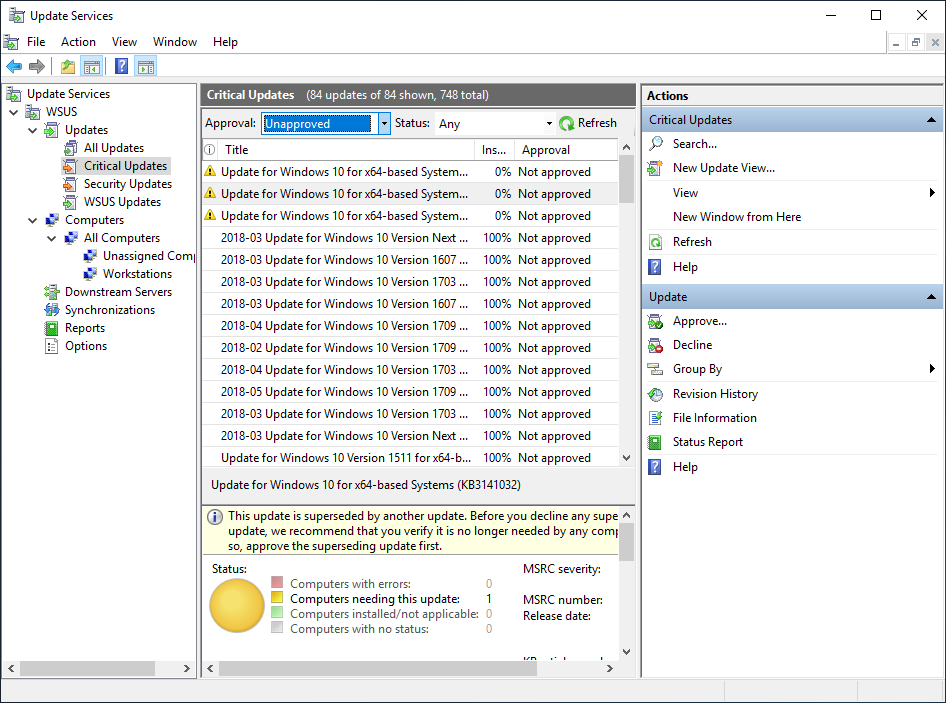
Same way, select security updates, and you would see the security updates ready for installation as in the below screen.
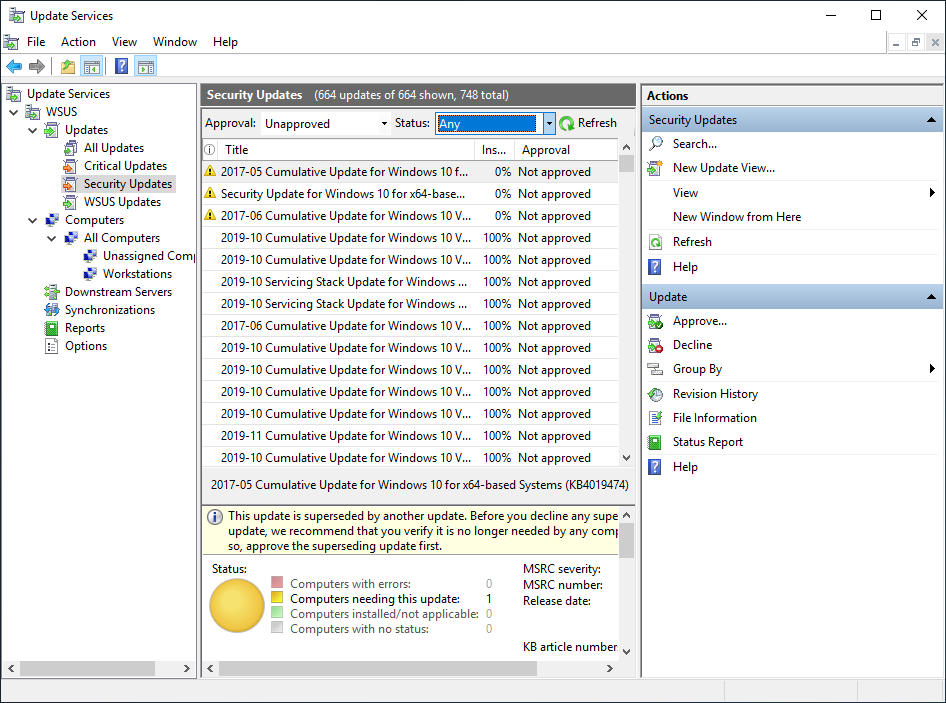
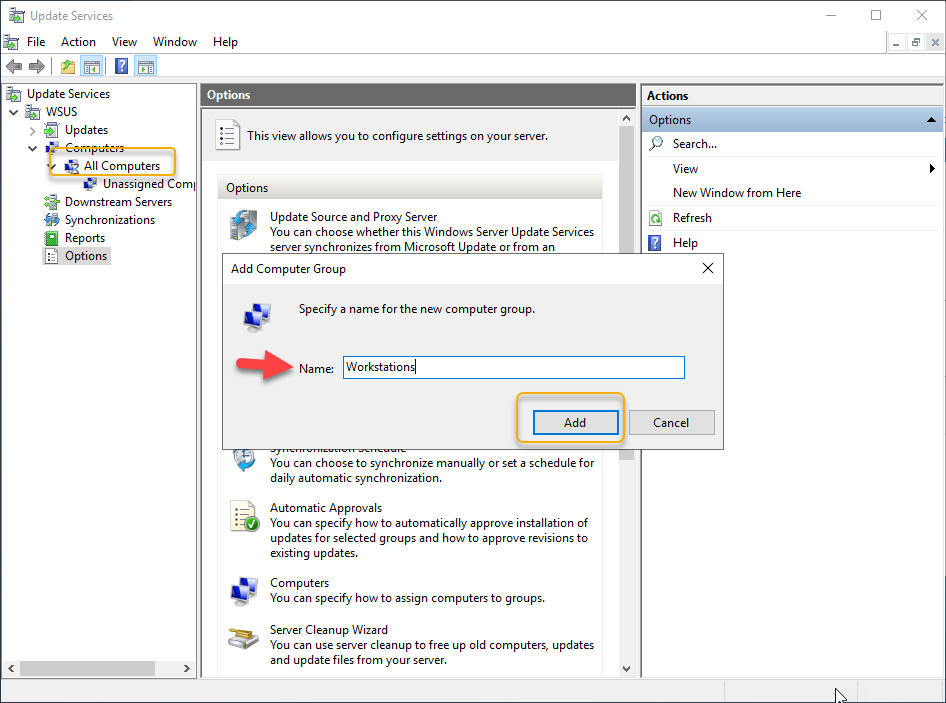
On the Computers hierarchy, we are going to create a group called workstations where all the workstation computers are grouped by client-side target GPO, which we are going to look at in the upcoming demonstration. On the All Computers node right-click and click Add computer Group and type a name, I am creating a group called workstations. Click Add to add the computer group.
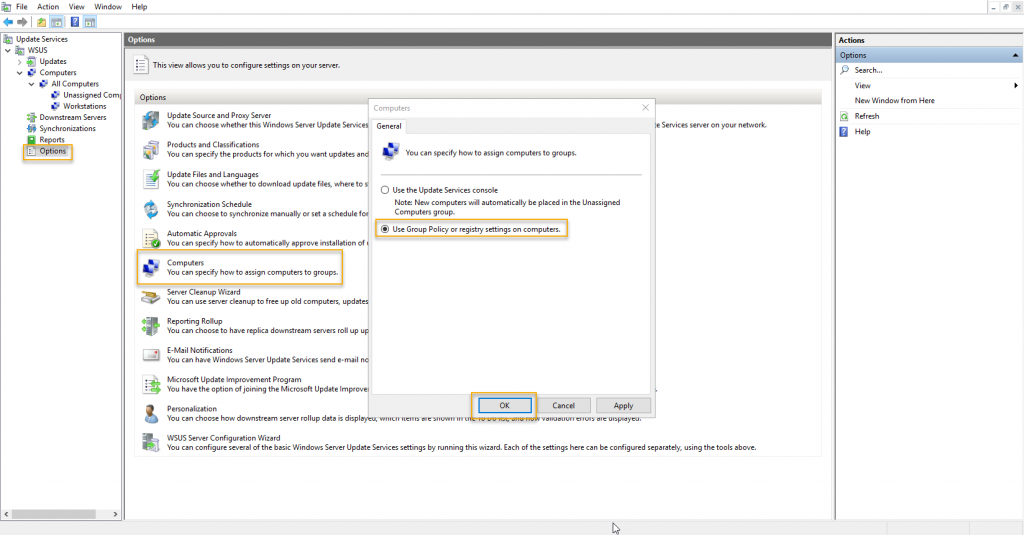
Apart from already configured from WSUS configuration wizard, we are also going to do a slight configuration change on the options navigation under computers. Double click Computers and select User Group Policy or registry settings on computers to assign the computers to the group with the help of client-side targeting to assign the computers to the group.
Configure the Group Policy object for WSUS Clients
To configure client computers automatically get the configuration details of the WSUS server, we are going to use the Group Policy object to update the configurations.
Login to Domain Controller and launch server manger. On the server manager snap-in click on tools and Group Policy Management to open Group Policy management console
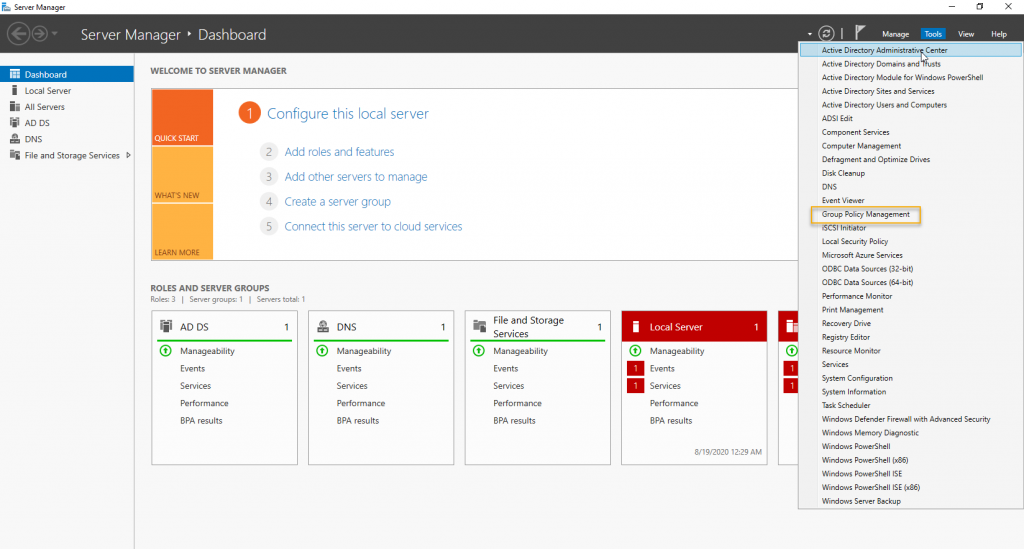
Right-click the OU where the Computer objects of the computers to which you want to configure WSUS and click create and link Group policy object to create and link a new Group Policy object. The Group Policy object happens to be Computers OU under Company root OU in this demonstration.
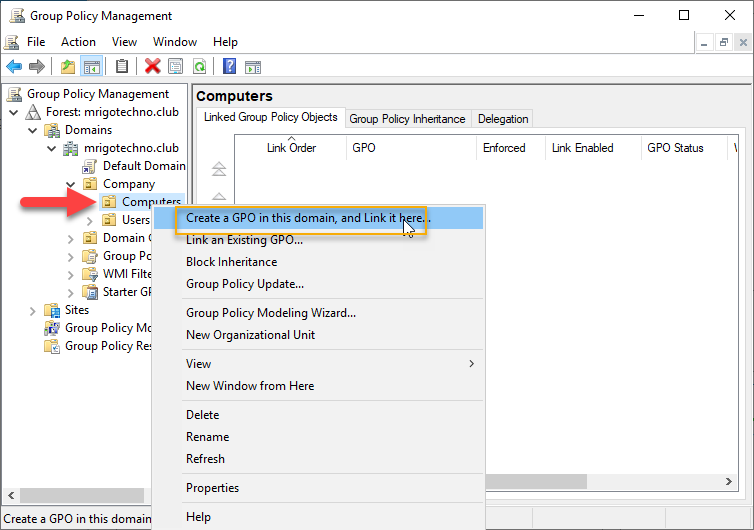
As this is Workstations Policy, I have given name as WSUS Workstations Policy. Type a name descriptive and click OK.
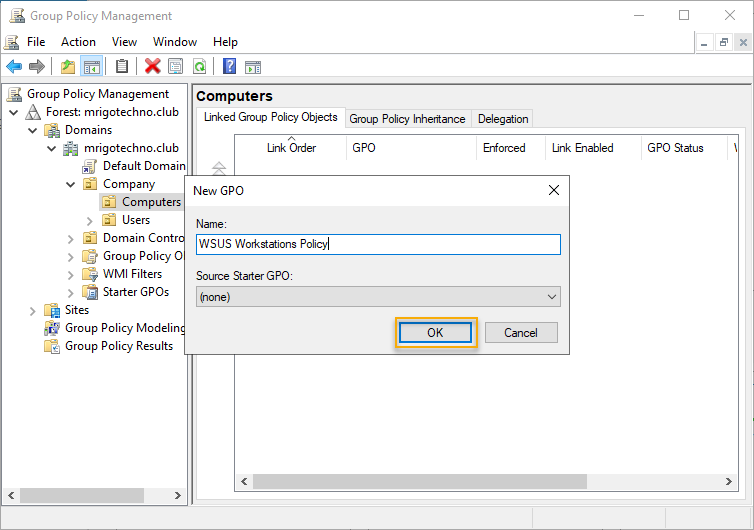
Right-Click the Policy created just before, and click Edit.
![Dutta has so far authored 16 books for adults, 13 of which are non-fiction while three are fiction.[5] His non-fiction books are based on a diverse range of subjects like The Brahmaputra published in 2001 by the National Book Trust; Cha Garam: The Tea Story revised and reprinted in 2013 by Orchid Publications; Unicornis: The Great Indian Rhinoceros published in 2001 by Konark; and The Roving Ministrel a biography on musician, singer and filmmaker Bhupen Hazarika, published by Rupa Publications in 2002.[6]
Anagarika's Swansong published in 2009 is a fictional novel by Dutta. Anagarika's Swansong is a satiric takeoff on the novel genre. This anti-novel debunks all the conventional elements that a novelist would otherwise employ, including a linear narrative, structural integrity, naturalistic characterization, emotional or situational conflict et al.
Anagarika in Sanskrit is one who renounces society and materialism in search of truth. In the book the author alludes to Prince Siddhartha who gave up his princely life to seek out in search for existential truths and to transform into Gautama Buddha, the enlightened one. The protagonist of The Anagarika's Swansong, is nameless and undertakes journey similar to that of Prince Siddhartha in the modern age to find the meaning of existence. However, because of his inferior intellect and he lives in Kaliyuga or "the era of untruth", he first lands up in to a local lunatic asylum, but finally stumbles into "poor man's enlightenment"![7]
The Ahoms published in 2016 is a historical fiction the delineates setting up of the Ahom Dynasty that ruled a large piece of Northeast India including all of present-day Assam. In 1228 A.D. an event occurred in the northeastern region of India, which not only changed the destiny of the Brahmaputra Valley and the surrounding mountains, but also of South East Asia. A group of Shan or Tai warriors, led by a brave leader named Sukapha, having left its original home in the Shan country in Myanmar, entered Upper Assam and set up the nucleus of what was later to become the powerful Ahom Empire. From the time Sukapha entered this region till it was annexed by the British in 1826, for nearly six centuries, his descendants reigned over a greater part of the Brahmaputra valley. Few dynasties in the world, let alone Asia, had enjoyed such a long period of almost unbroken rule. It was primarily due to the Ahom dynasty that the pre-colonial Assamese nation was born. Its reign witnessed the synthesis of the disparate tribes inhabiting the Brahmaputra Valley and the evolution of a distinct Assamese language, culture and nationalist identity. The Ahom Dynasty was one of the greatest political entities in medieval Asia, equal if not greater than the more well known counterparts in China or Japan. Its history is replete with tales of war, bravery, brutality, love, loyalty, treachery and treason. This book, The Ahoms, seeks to imaginatively acquaint readers with the saga of this fascinating dynasty and provide a glimpse of the major events during its six hundred year rule.[8]
Red Camellia Green published in 2016 is Mr Dutta's second fictional novel. Henry David Esscombe, a pioneer tea planter, comes to Assam in the latter half of the 1850s and opens out the Dhanboa Tea Garden. However, the unhealthy Assam environment takes its toll and, gravely ill, he summons his son David to take over the plantation. His daughter, Cordelia, desperate to see her dear papa again, accompanies her brother to Assam. As the brother-sister duo struggle to adapt to the changed circumstances, a host of individuals, including the phlegmatic Michael Bailin, the devilishly charming Christopher James Buckingham, the self-confessed anarchist Reverend Garry Swanson, the Assamese nobleman Gokuldeva Barua, the defiant conscripted tea workers Bircha and Meghu and a host of others, intrude into their lives. Against a backdrop of tea plantation life in the 1860s and the barbarous conditions whereby migrant workers were lured and enslaved, a chain of events unfold in this epical novel, leading to an unexpected, explosive climax which turns red the green leaves of Camellia.[9]](/wp-content/uploads/2020/08/38.png)
We are going to enable three Group Policies in the following GPO Section.
Computer Configuration -> Policies –> Administrative templates-> Windows Component-> Windows Update
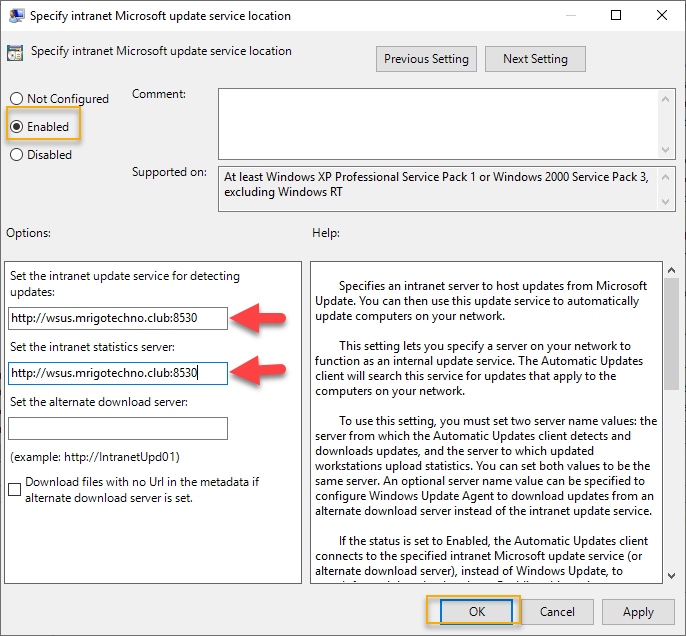
The first one we are going to edit is “Specify Intranet Microsoft update Service location,” double click on it.
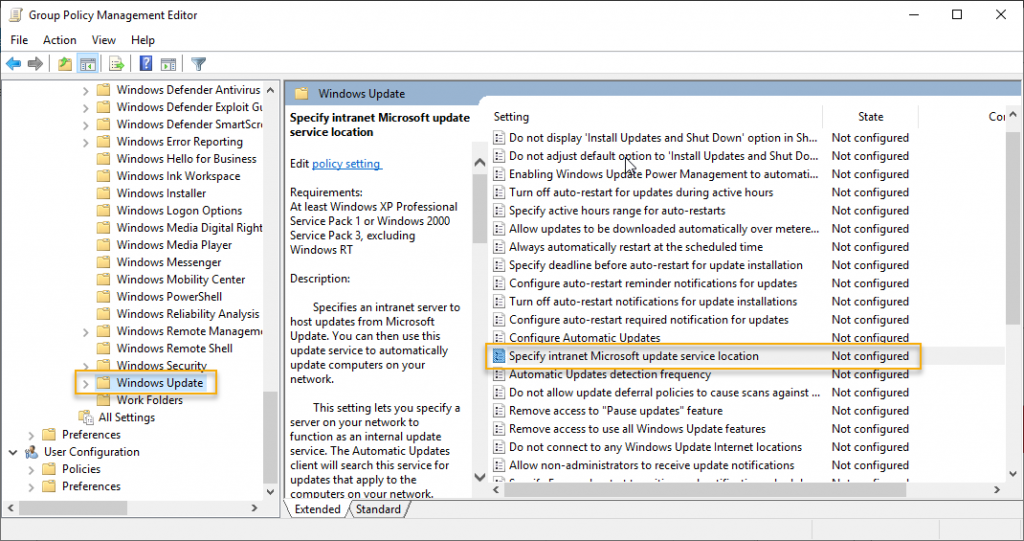
Click enable to enable this setting and type the URL of the WSUS server. In this demonstration, the server name of WSUS is WSUS.mrigotechno.club. Replace this hostname as per your installation and add 8530 to it. So the URL to provide on Set the intranet update service for detecting update and set the intranet statistics server is http://wsus.mrigotechno.club:8530
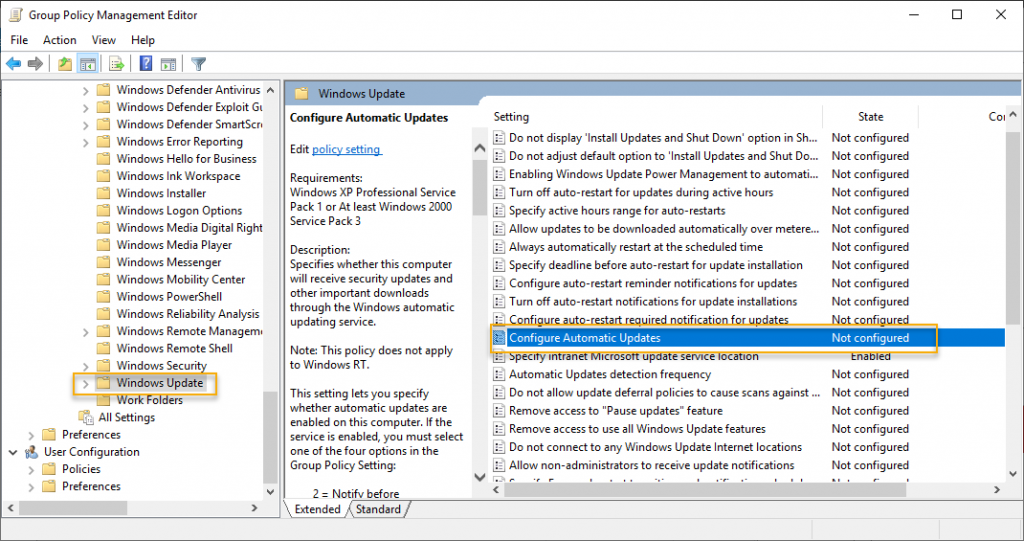
The Next setting is “Configure Automatic Updates,” double click to edit the setting.
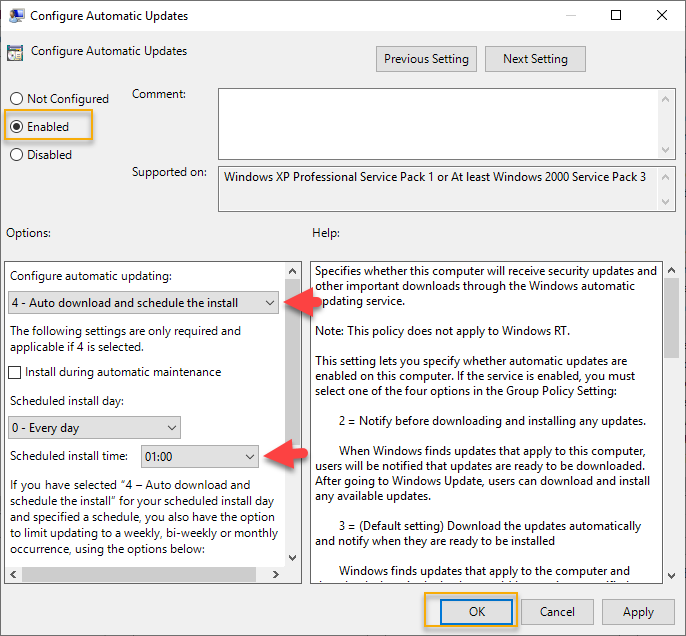
Click Enabled to enable the setting, and in the options section, select one of the four options which match your environment. The auto downloads and schedule the install under configure automatic updating is the good option as there is less overhead on the administration point of view. Also, select a time to schedule install. Click OK to go back to the GPO settings list.
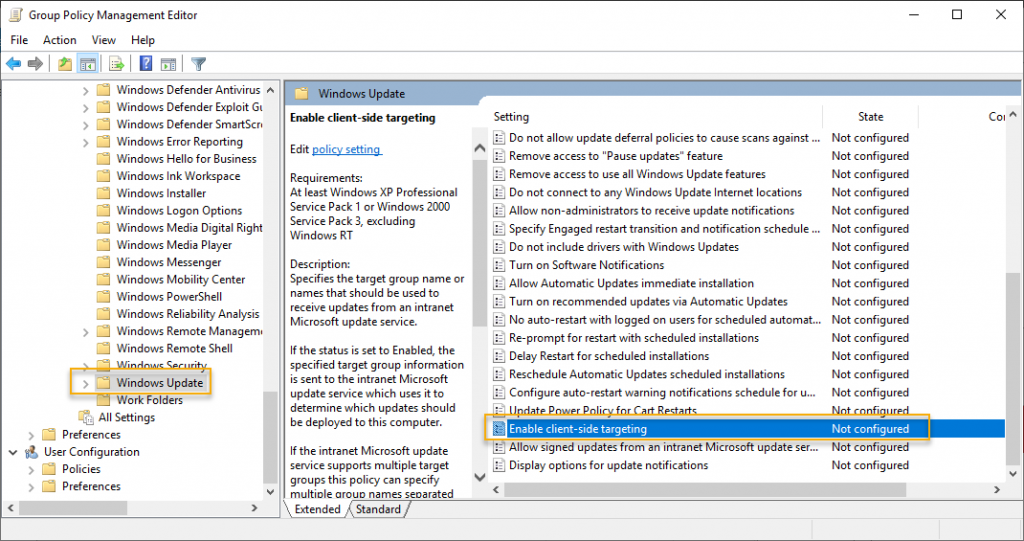
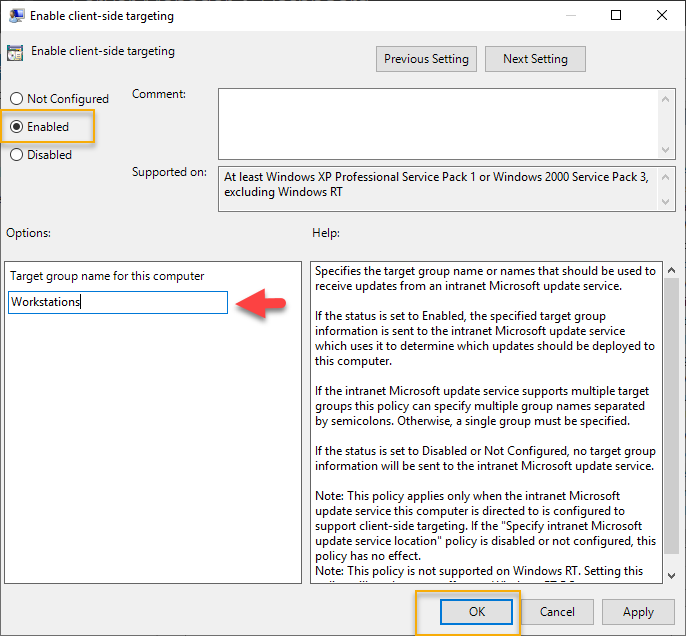
The third setting is client-side targeting. Double click on the “Enable Client-Side Targeting” setting.
On the Client-Side Targeting settings, click enabled to enable these settings and type the group name that we created for the group created on the WSUS console previously. The group name was workstations, and you type the name that you have created and click OK
Testing WSUS Client
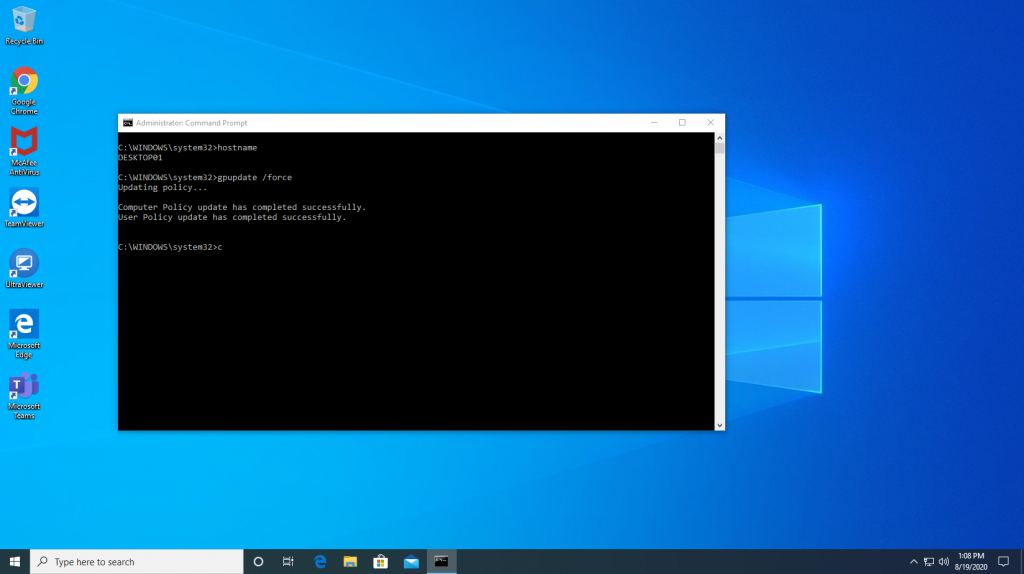
We have completed setting up Group Policy. Now I’m going to start the Client computer installed with Windows 10 and joined to the Active Directory domain. Open a command prompt and type the following command to get the group policy update.
gpupdate /force
You can see the command output as in the screen below on the Windows 10 computer.
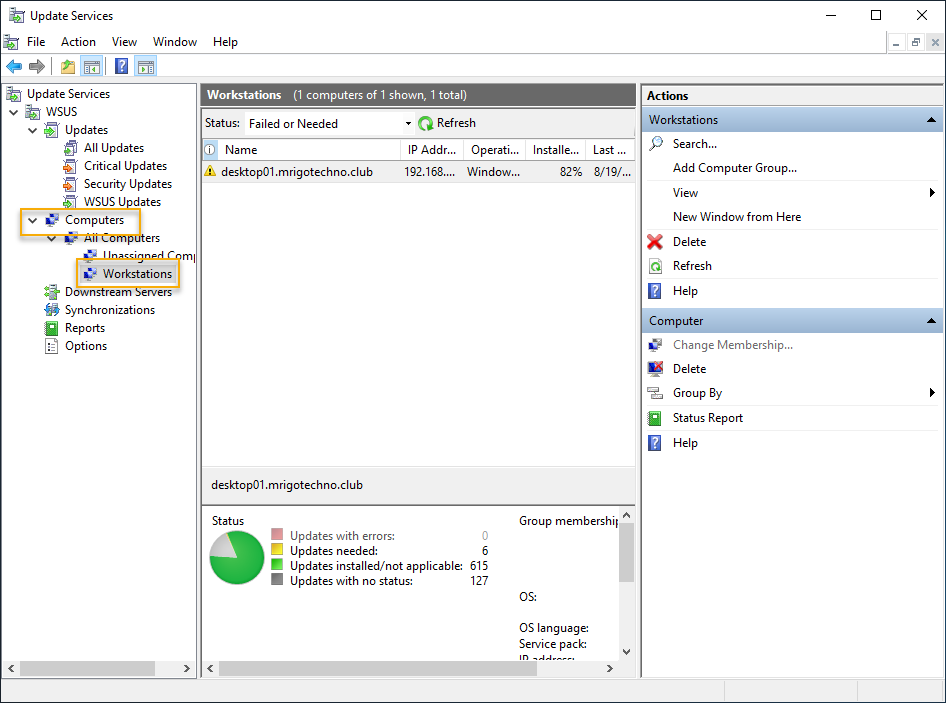
Once the group policy is updated on the client computer, the client’s computer name and update status visible on the WSUS console under Computer Group, which happens to be client-side targeting.
Conclusion
This is the end of the Windows Server Update Services demonstration. In this article, we have covered installing the WSUS role and Configuring WSUS using configuration wizards. Once the WSUS installed and configured computer group created and Group Policy Object created on the Group Policy Management console on the domain controller. The Windows client computer tested with WSUS as the final verification of the WSUS deployment.
I have demonstrated other roles of Windows Server 2019 in Get An Admin article. You may have some questions or feedback to share with me, please click the comments below and share your thoughts. I am so happy to answer your questions.