Preface
This is a demonstration article to deploy Windows Server 2019 as Certificate Server in an Active Directory Domain environment where the server is configured as Root CA on Enterprise Certification authority. The demonstration has been started with the Domain Server installed with Active Directory Certificate Service role and configured as Certification Authority, Certification Web Enrollment, Certificate Enrollment Web Service, and Certificate Enrollment Policy Service role services. After Installing Certification Service Role and their role services the group policy object has been configured to enable organization computers to authentication the user’s workstation with a Workstation Authentication Certificate Template. The workstation authentication has been tested by a domain-joined computer updated with the group policy.
When you are ready let’s get started with installing the ADCS roles on the server manager console and continue configuring the certificate server moving on,
Add Active Directory Certificate Server Role
You can install the Active Directory Certificate Service roles as a Standalone CA on a workgroup computer or Enterprise CA on an Active Directory domain environment. The Root CA is the top hierarchy and Subordinate CA is right next to the Root CA. If you want a more secure environment for Certification Authority installation, you can install a Root CA and then Subordinate CA and take the Root CA offline to make it more secure. The subordinate CA requires the Root CA only when the Certificate service is installed on it. After installing subordinate CA, the Root CA is not required as all the certificate requests and other processes will be handled by the subordinate CA.
In this demonstration to make the environment simple and make this article for small to a medium office environment, we are installing only Root CA on an Enterprise CA setup. The Active Directory Domain Services is already up and running on this network, so we are skipping the ADDS installation or assuming the ADDS setup on your network is already running. So, the demonstration starts with the Certificate Server manager console. To make the demonstration understandable and easy to follow even for a newbie, I have not skipped any screenshot on the way of installing and configuring this certificate Server. If you follow this article you can easily install and configure Certificate Service on your Active Directory domain setup. I hope you are very much convinced and let us start the demonstration and just follow on from this point.
Launch Server Manager and click Add Roles and Features on the middle of the console.
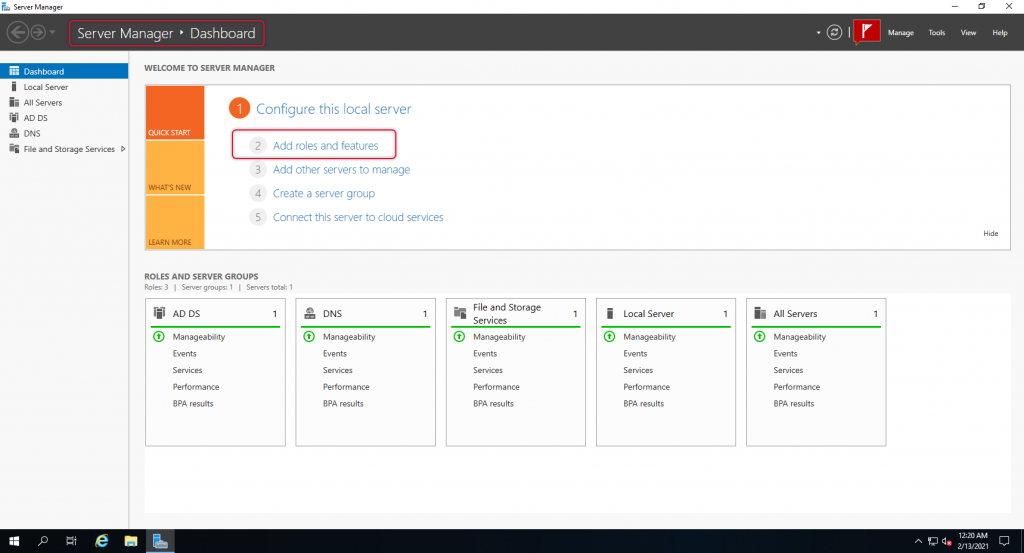
On the Installation type selection screen point to the “Role-Based or Feature-based Installation” radio button and click Next.
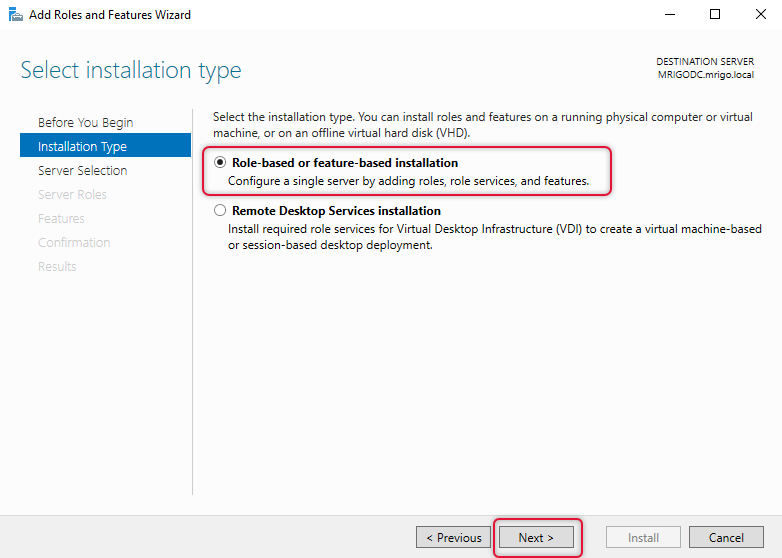
On the destination server selection screen leave the local server selected and Click Next
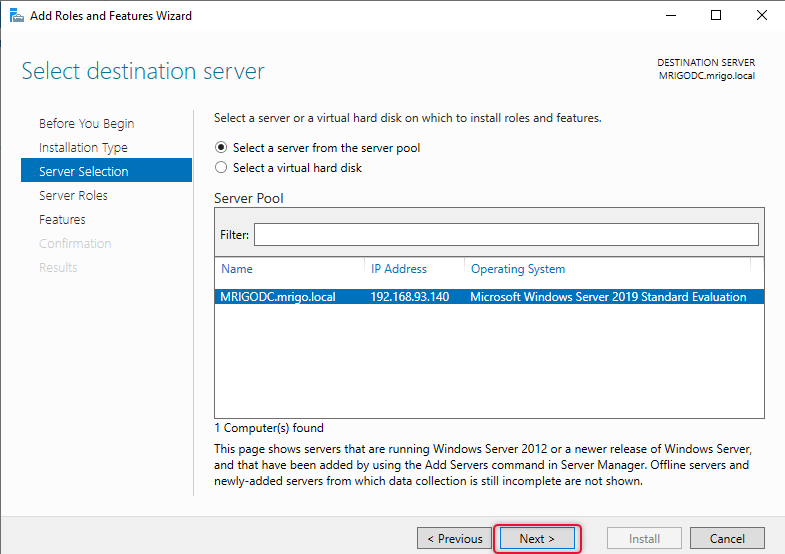
On the Select Server Roles Click on the Active Directory Certificate Services check box, when you click this check box immediately the pop-up would show up to add Features related to it. Click Add Features
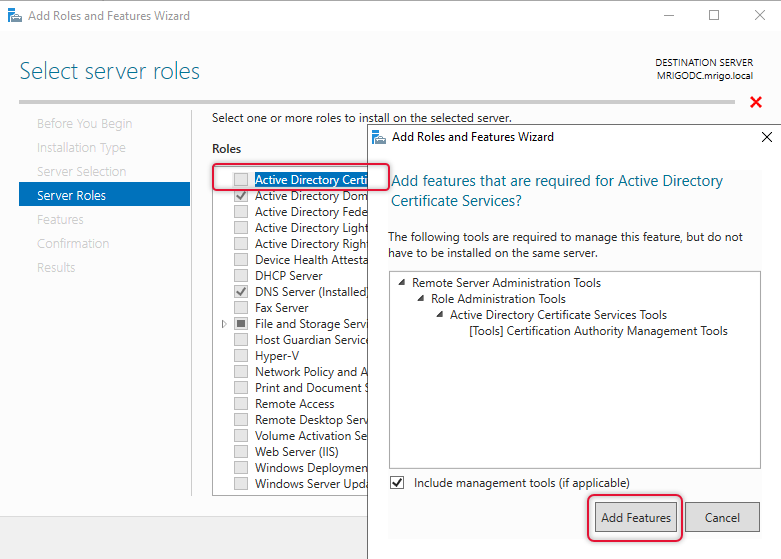
The Active Directory Certificate Services role selected and Click Next to continue.
On the next screen to select Features, just leave the features selected default and Click Next.
On the next screen you will be shown with a note about Active Directory Certificate Services and what it will do, so if you are new to ADCS, go through the note that will help you get some information about it. Click Next to continue.
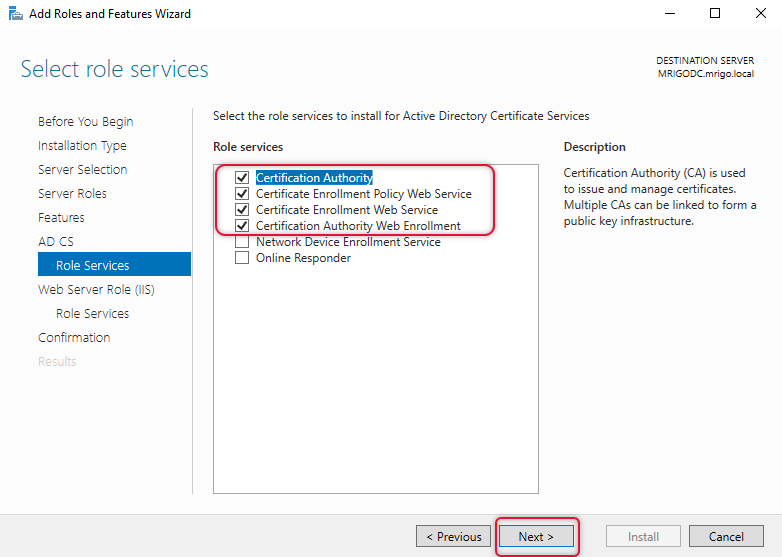
On the Role Services selection screen, select Certification Authority which the main reason we installing this server Certificate Authority we enrollment, which is making some manual certificate enrollment easy for administrators. The other two Certificate Enrollment, that is web Service and policy web service would be useful for enrolling the non-domain joined device in your network such as Access point, a network switch, and so on. Leave the other two roles for now, and click next to continue.
The next screen is an informative note for web server roles just as we see ADCS role info a little bit back in this demonstration. Click Next to continue.
The default web server roles are only required to install this service, so click next to continue.
On the Confirm installation selections screen, all the selection install the role so far will be listed just browse through the features and click next to continue.
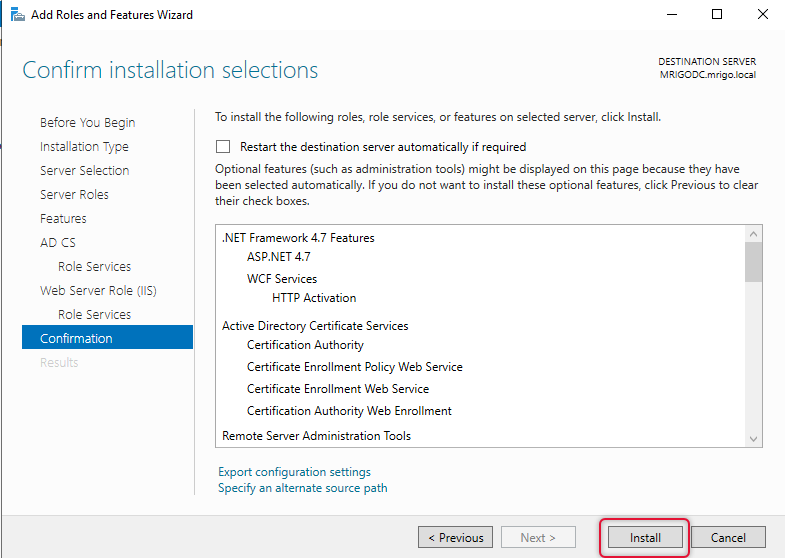
In the installation progress screen shows the installation is complete, click on the link in the middle of the progress window to configure ADCS on this server. Click “Configure Active Directory Certificate Services on the destination server” and the ADCS configuration wizard will start and follow on with that screen to configure it.
Configure Active Directory Certificate Services
The currently logged on user account will be taken by the configuration wizard as a role configuration account, make sure the account is Domain Admin of the root domain and Enterprise admin of the forest and click next to continue.
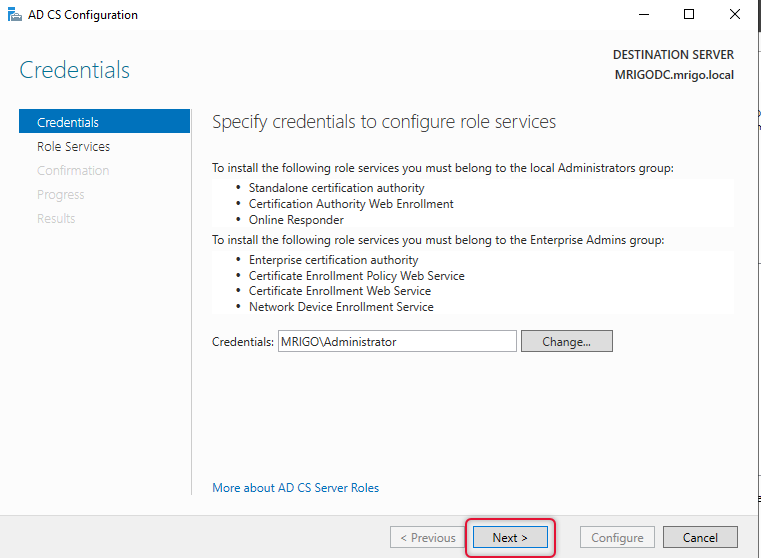
You can only select Certification Authority and Certification Authority web Enrollment role services and click Next.
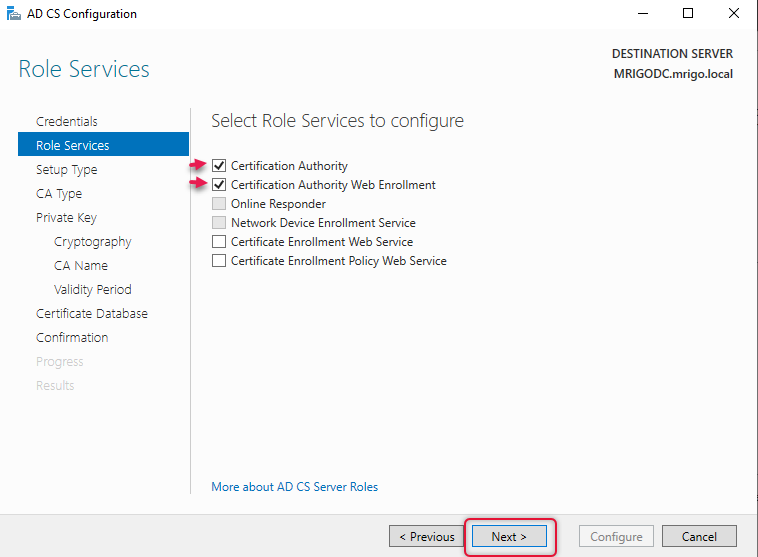
As this is an Active Directory Domain environment I have chosen Enterprise CA for the CA type, click Next to continue.
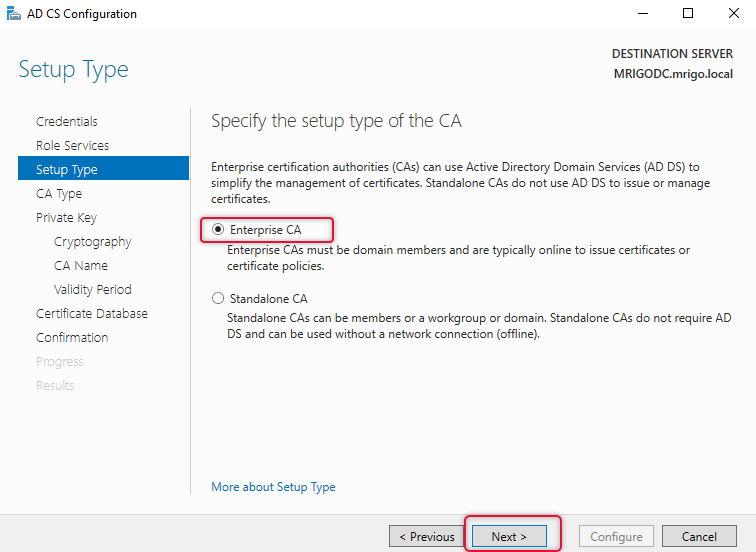
As this is the First Certification Authority Server in the network and this is only one CA server, select Root CA and click Next.
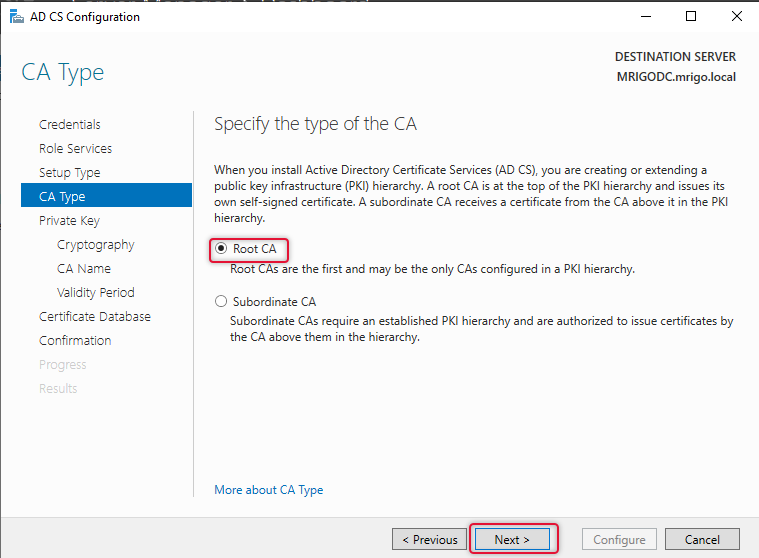
As this is the Root CA, select Create a new private key and click next.
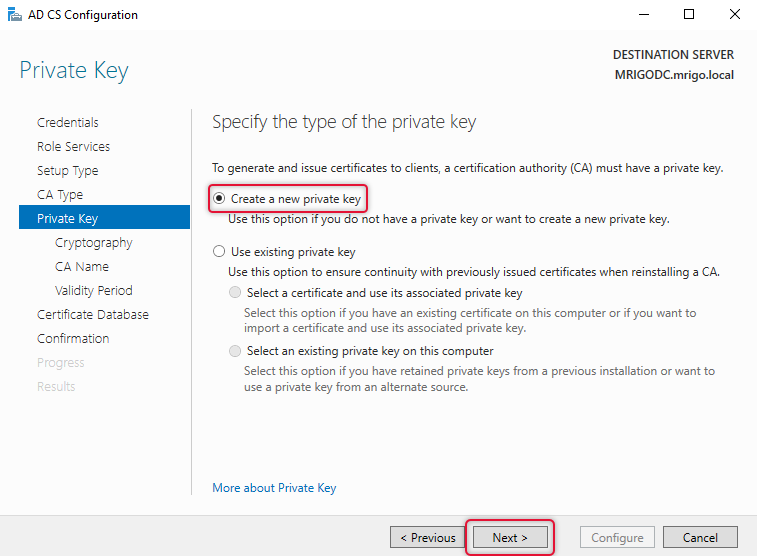
Leave the default RSA as a cryptographic provider and pick the maximum key length for better security and SHA 256 as an algorithm as most of the devices support this algorithm.
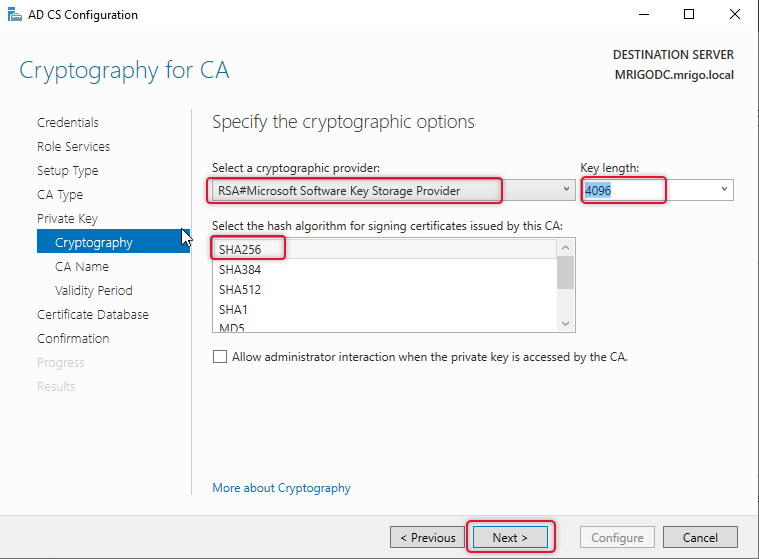
Give a Descriptive CA name I have given my organization name added CA to identify the Root CA.
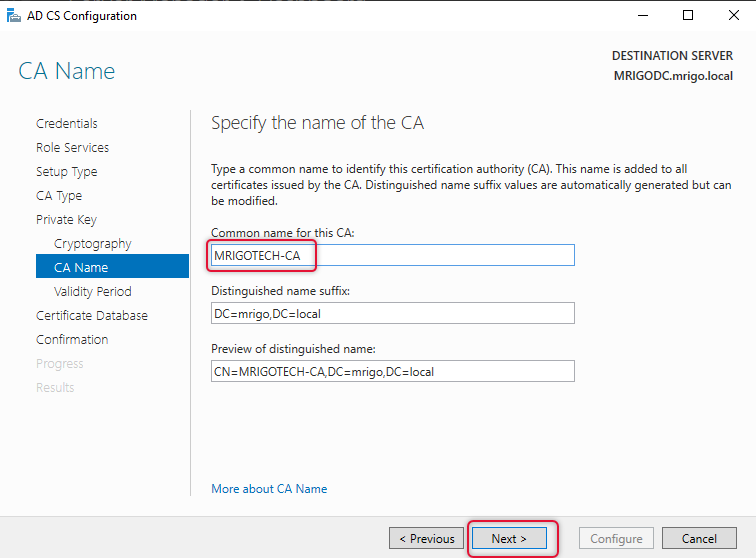
Make the validity at least 10 years as it will give some room for the Root CA will be operating on your network without renewing it. You can make it valid as much as you want.
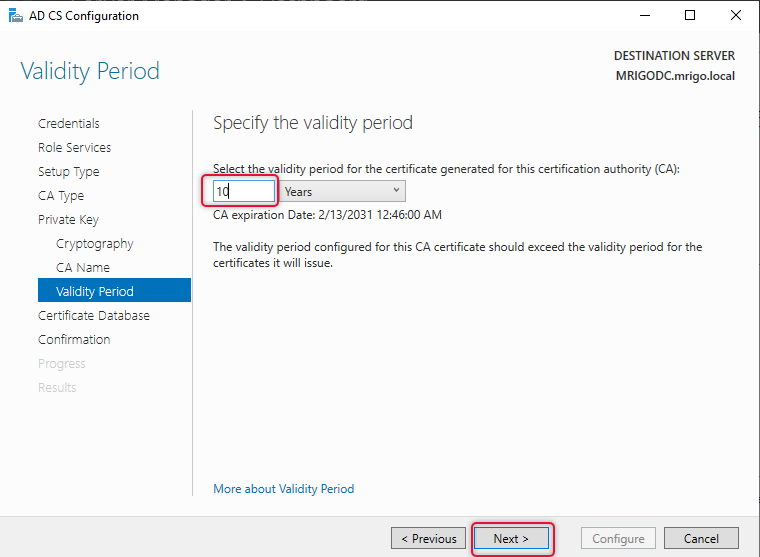
You can change the certificate database and log path to a separate disk. But you can leave the default path for small and medium environments.
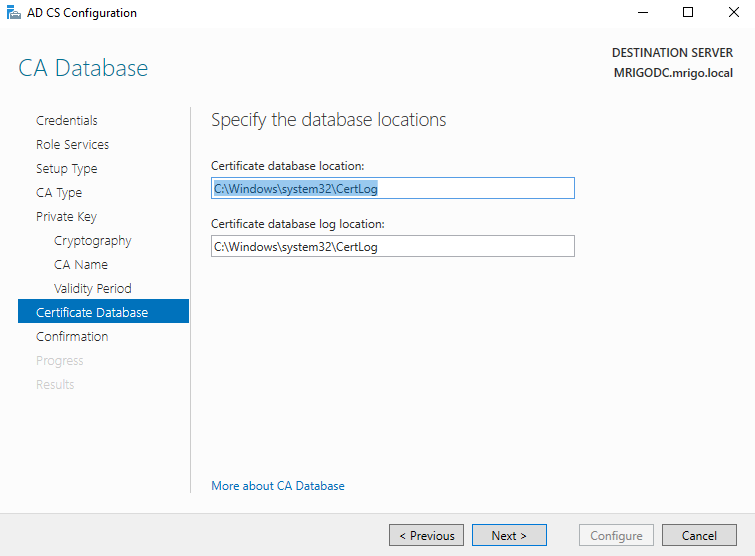
On the confirmation screen you will be listed with all the selections done so far and if you are happy with the selection click to Configure to start the configuration.
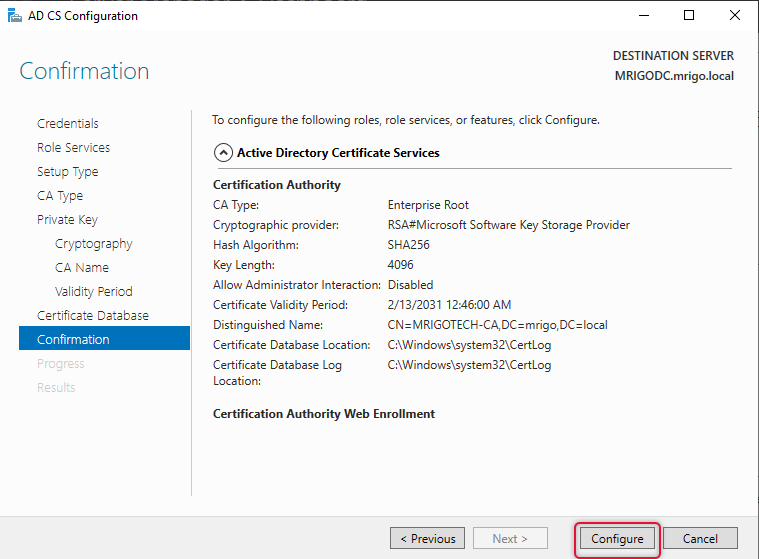
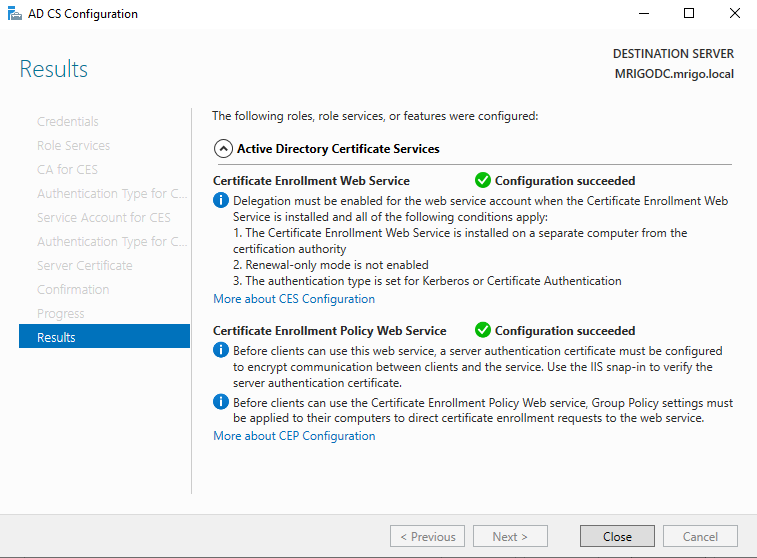
On the Results screen, you would see the Configuration Successful for both the role services and click close.
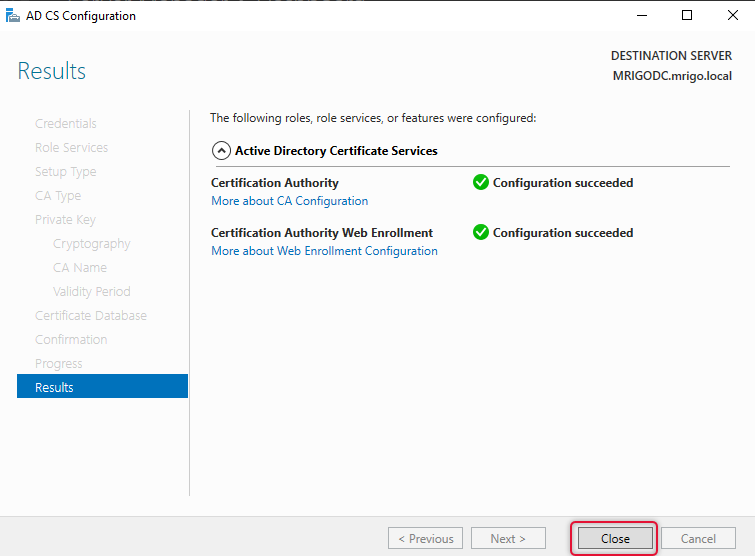
Once you click close a pop-up will appear and it will prompt whether you want to configure the rest of the two services. Click Yes and move on to configure Certificate Enrolment web service and policy web service.
Leave the administrator account selected on the next screen and click Next.
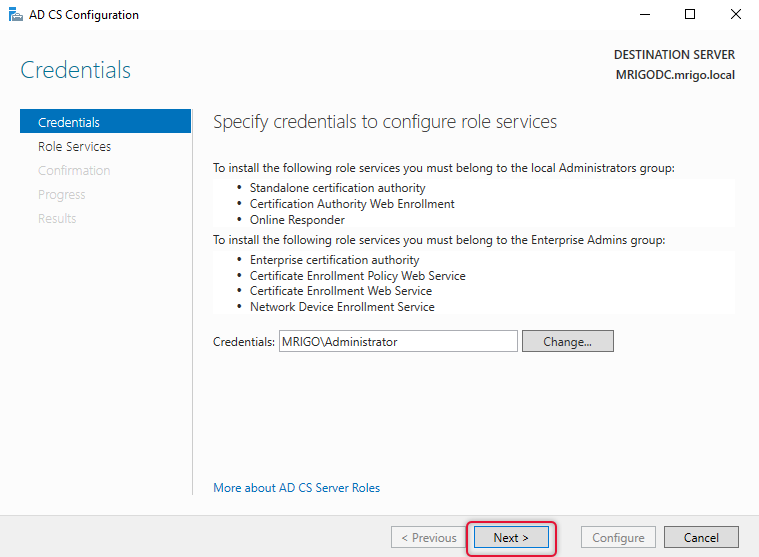
On the Role Services selection screen, click the rest of the two role services, that is Certificate Enrollment web service and policy web service and click next.
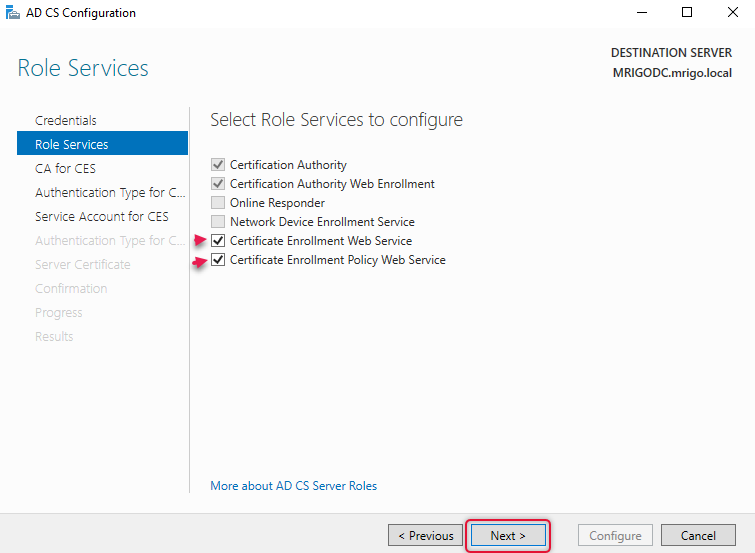
As we have already configured Root CA on this Server the CA name will be taken automatically, check the CA name and click next to continue.
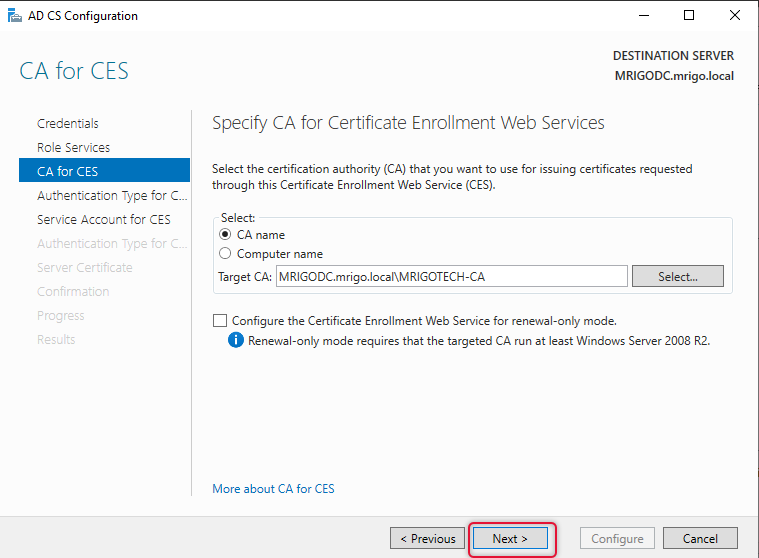
You can choose one of the three authentication methods, as we have Active Directory already in place, it is wise to select Windows integrated authentication. Once selected your preferred authentication, click next to continue.
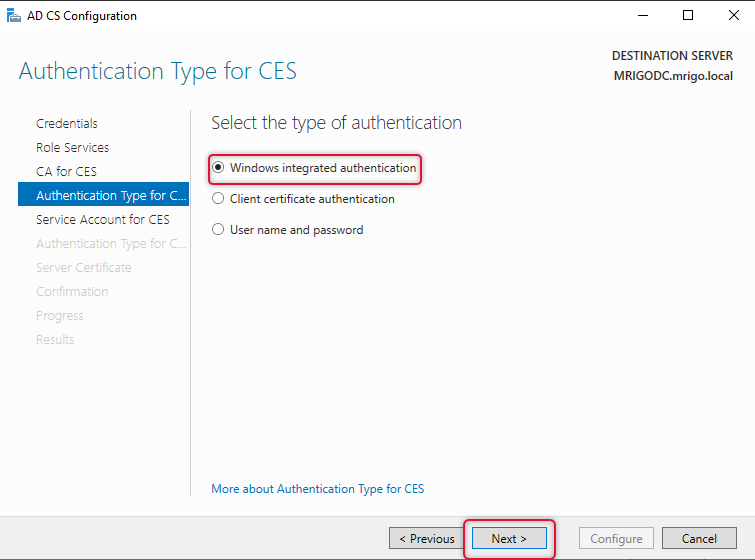
You can create a service account for certificate enrollment web services (CES) and provide that account details here, as this is a demonstration, I have chosen App pool identity for this service to run. Click next to continue.
We have specified certificate enrollment web services, not we are going to an authentication method for certificate enrollment policy web service. Select an appropriate authentication method, choose windows integrated authentication if you are not sure which authentication method to use. Click next to continue.
On the select server authentication certificate, the root certificate we have configured in the previous configuration will be shown existing certificate SSL encryption, click refresh and click next to continue.
On the confirmation page check all the role services and features selected on this wizard and click configure to configure them.
On the Results pane, you would see the configuration succeeded and click close to close out the configuration wizard, and go back to roles and features installation.
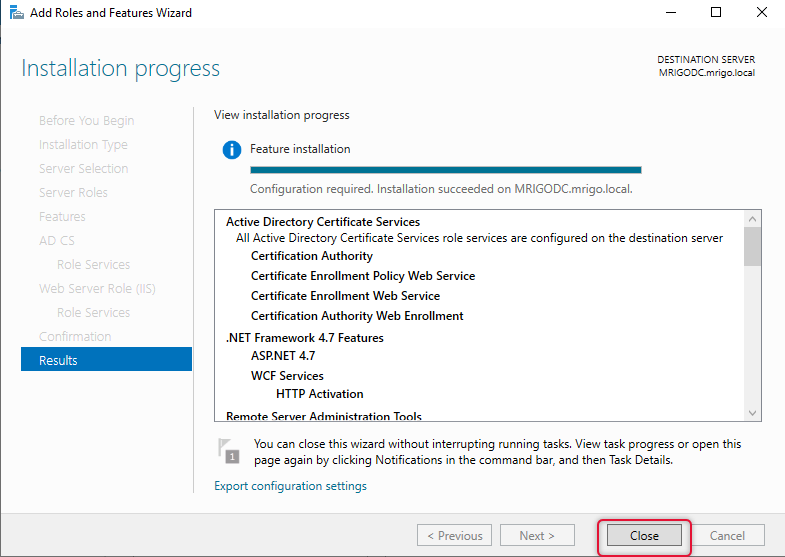
Click close again on the Active Directory Certificate Services installation window if you have not closed it yet. Now the Active Directory Certificate Services role has been added and roles services have been configured.
Enable Group Policy Object to auto-enroll workstation authentication.
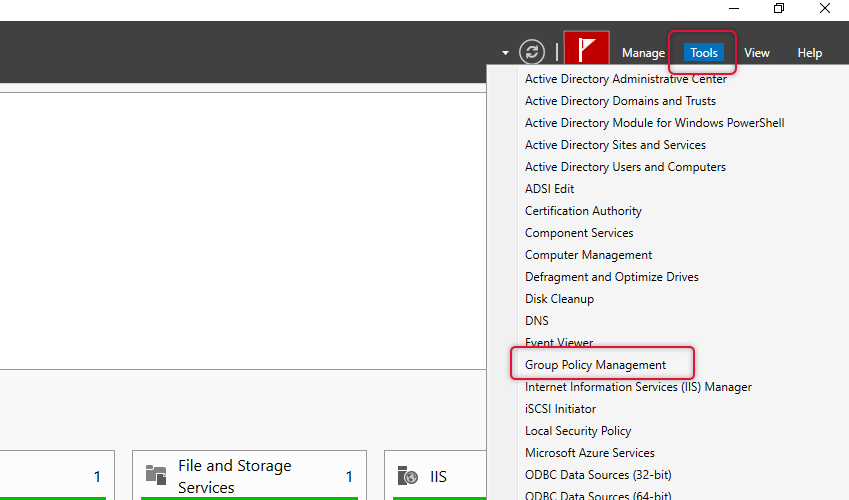
Open Server Manager and select Group policy management from the tools menu.
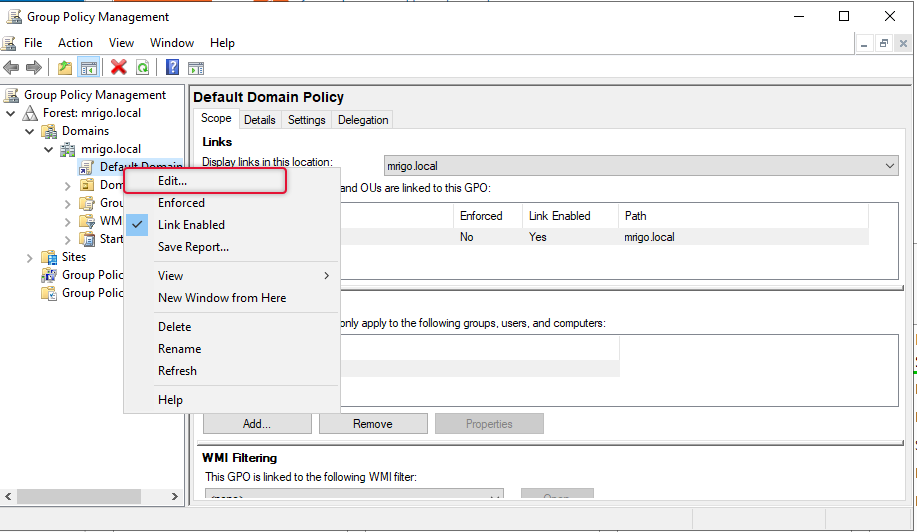
Point to Default Domain policy and click edit to modify the policy.
The group policy management editor windows will be opened and go to Computer Configuration/Policies/Windows Settings/Security Settings /Public key policies and double click the object Certificate Services Client – Auto-Enrollment as in the screen capture below.
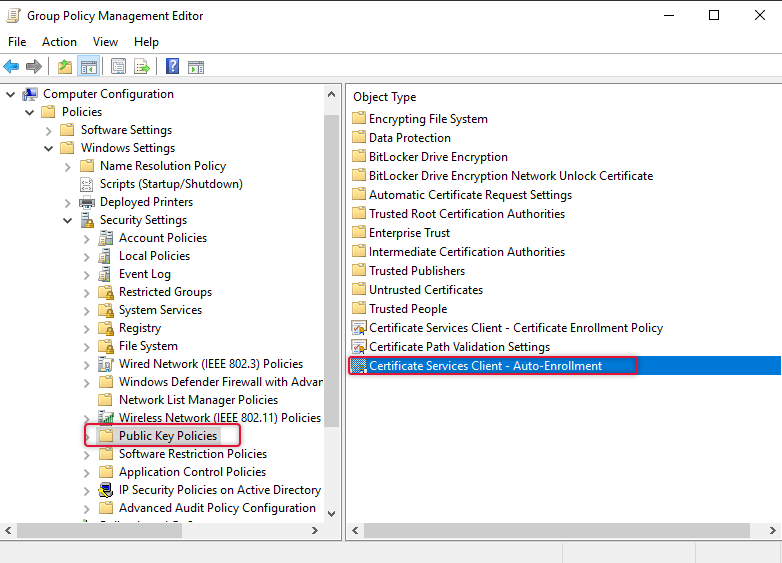
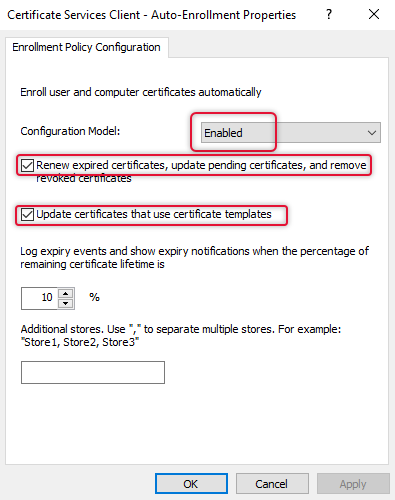
On the Configuration Model, select Enabled. And select the checkboxes below.
Renew expired certificates, update pending certificates, and remove. Update Certificates the use certificate templates.
Once these two checkboxes are checked click OK.
The GPO for workstation authentication is completed. Go to the Certification Authority management console to create a workstation authentication template.
Configure Workstation Authentication
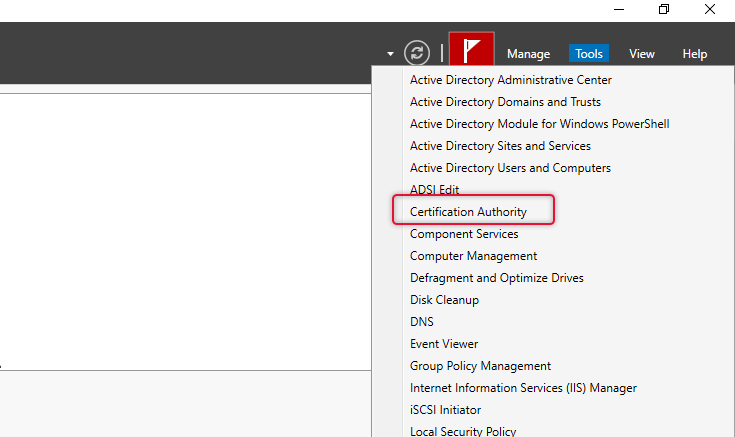
Go to Server Manager and launch Certification Authority from the tools menu to configure the workstation authentication template.
Select the Certificate Template and right-click and select Manage on the menu list.
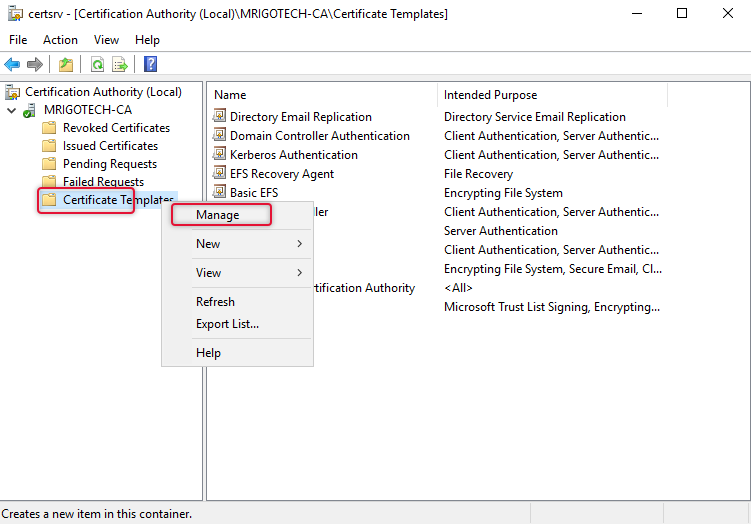
As we are going to do some modification on the workstation authentication template it is wise to duplicate that template so the original template will not be modified if we need to use the template again for some other purpose or misconfigured by mistake could not get it back to the default configuration. Right-click the workstation authentication template and click Duplicate Template.
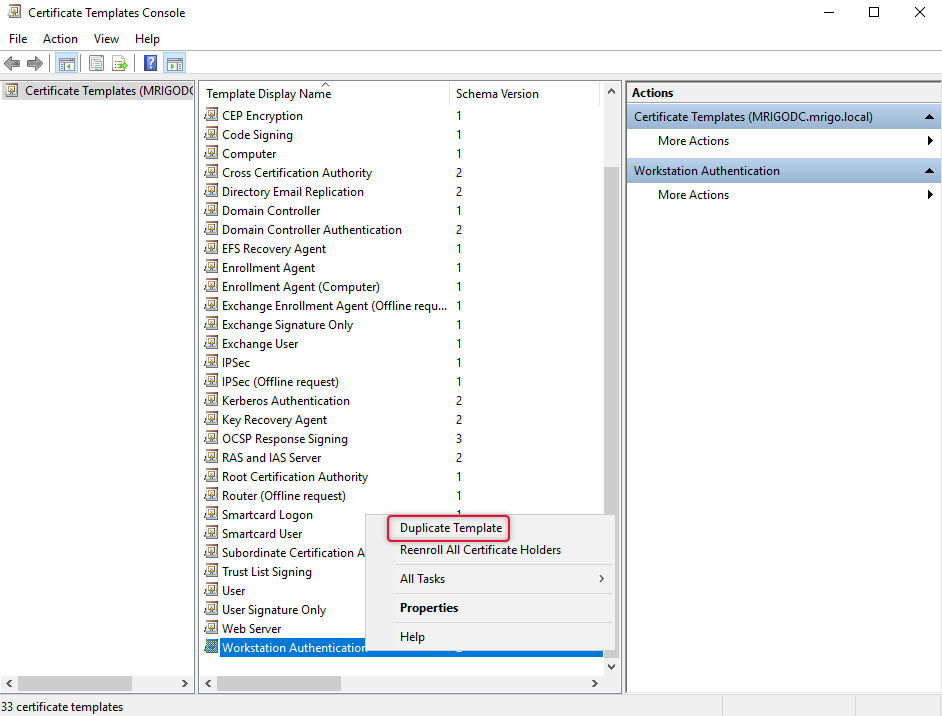
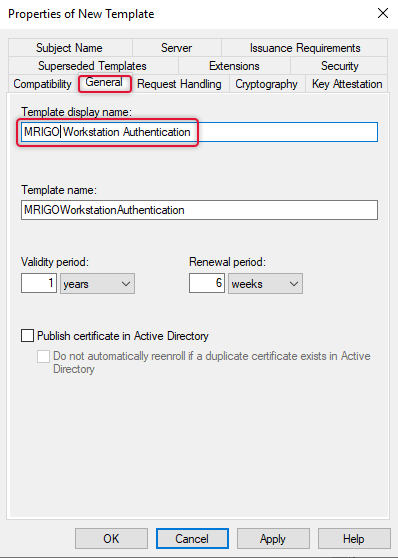
On the Properties of the Template, go to the general tab and give a descriptive name for the template I have given the organization name followed with the template name.
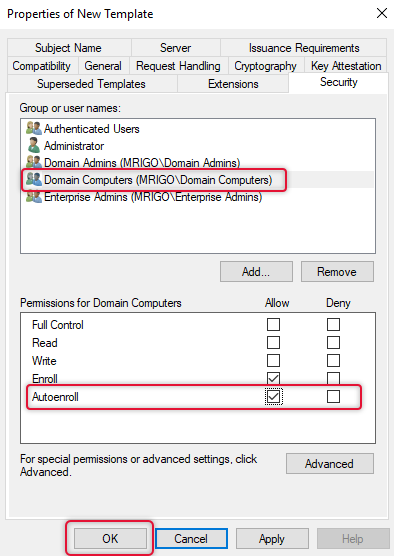
Then go to the Security tab and point to Domain Computers group name and select Autoenroll check box and click ok.
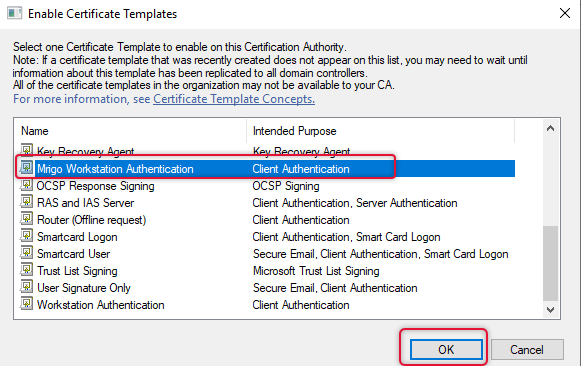
We have created a duplicate of the Workstation Authentication template and configured it, now enable the template to issue. Right-click the Certificate Template and select Certificate Template Issue from the New subtree.
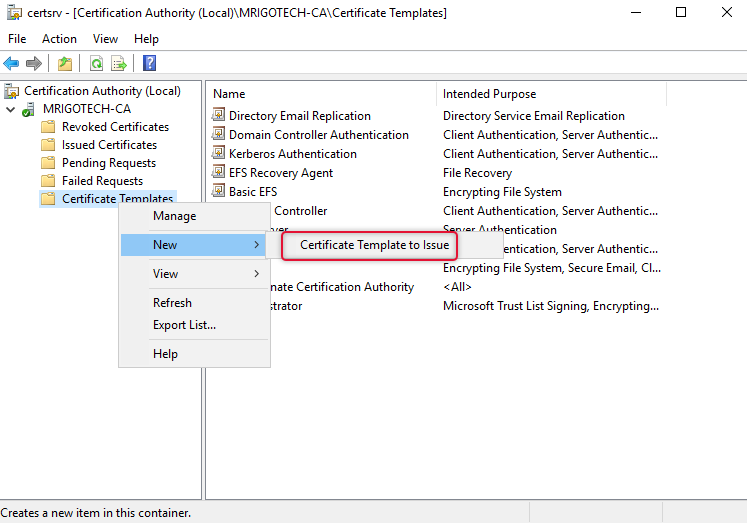
Select the newly duplicated template and click OK.
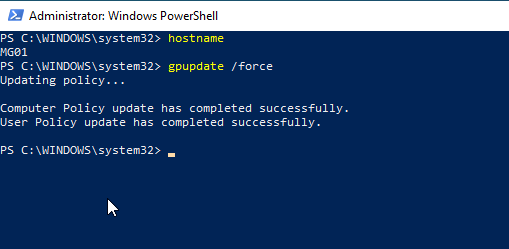
To test go to a client computer such as Windows 10 and run the command gpupdate /force.
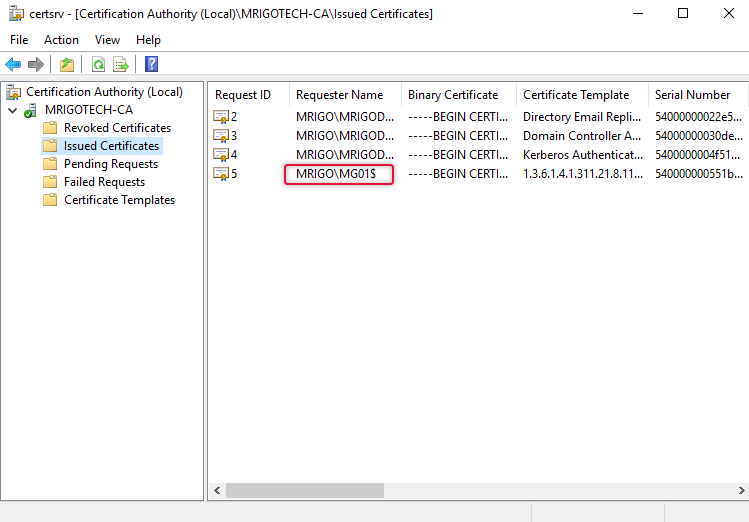
Once the group policy on the client computer is updated the certificate of the workstation can be found on the issued certificates list on the Certificate Authority management console.
Conclusion
In this article, we have gone through Active Directory Certificate Services role installation and then configured role services of the Certificate Services components. After installing the roles services and configured them, we have enabled the GPO for client authentication for workstation authentication and enabled the template by duplicating from the template node on the certification authority management console. This concludes the Certification Authority deployment and Active Directory Certificate Services up and running on our network environment. I hope the demonstration above is easy to follow and you understand the subject better than before.
I have a lot of happiness in getting your feedback on this article and your feedback will encourage me to write a lot more articles like this. Please post your comment below, I will see you next time in a different article.

